Hackers are stealing more info than ever. These 4 actions protect you
Massive data leaks and breaches are continually piling faster upon each other—just in the last month, we learned about a few billion records lost through National Public Data, another few million through Medicare, and 100 million through MC2 Data. Companies that handle background checks and other data processing services just aren’t securing the sensitive data flowing through their fingers.
Unfortunately, we the public must take the brunt of the consequences, which comes in the form of higher risk of fraud, identity theft, account takeovers, and other schemes seeking to rob of us our money.
But you don’t have to leave yourself open to such attacks—at least, not wide open. You can make it more difficult for bad actors to steal from you. Because your time is just as precious as your cash, and trying to recover from a successful scam can take both from you.
Make your login methods strongerThe more that passwords leak onto the internet, the easier it becomes for hackers to guess what yours might be. Not only can they feed that data into their cracking tools, but they can also use the passwords for credential stuffing attacks—that is, plugging in known email and password combinations around the web to see what accounts can be accessed.
So at minimum, you need passwords that are both strong and unique to safeguard your accounts. (A password manager can help you keep them all straight.)
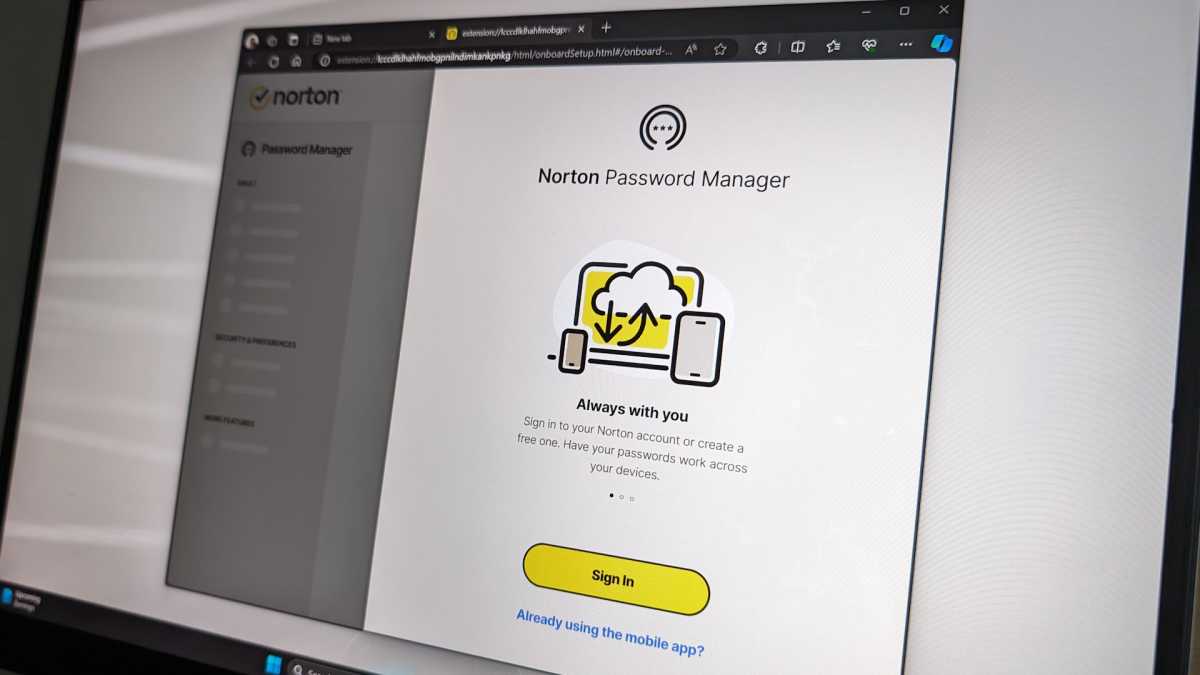 Choosing a password manager can be as easy as using the one included with a good paid antivirus software suite.
Choosing a password manager can be as easy as using the one included with a good paid antivirus software suite.
 Choosing a password manager can be as easy as using the one included with a good paid antivirus software suite.
Choosing a password manager can be as easy as using the one included with a good paid antivirus software suite.Chris Hoffman/IDG
 Choosing a password manager can be as easy as using the one included with a good paid antivirus software suite.
Choosing a password manager can be as easy as using the one included with a good paid antivirus software suite.Chris Hoffman/IDG
Chris Hoffman/IDG
But even a good password can’t keep out intruders if someone obtains or guesses it. You really want stronger protection—which is where two-factor authentication and/or passkeys come in.
Two-factor authentication (2FA) adds a second hurdle for hackers to clear before account access is granted. Most commonly, an app that generates a one-time code is used as a method for 2FA, but an even more secure method is a hardware dongle like a YubiKey. As a physical item, someone would need to have it in their possession to use it.
(Note: You can use codes sent to you by email or text message for 2FA, but they’re weaker methods, as SMS and email can be intercepted.)
Alternatively, you can skip passwords all together by using passkeys instead. This newer login method is more secure than passwords and less hassle than 2FA. Because passkeys are encrypted and tied to both the device and the website they’re created for, they can’t be stolen through phishing or used across the web like a password. You also authorize use of the passkey through biometric or PIN authentication for added protection.
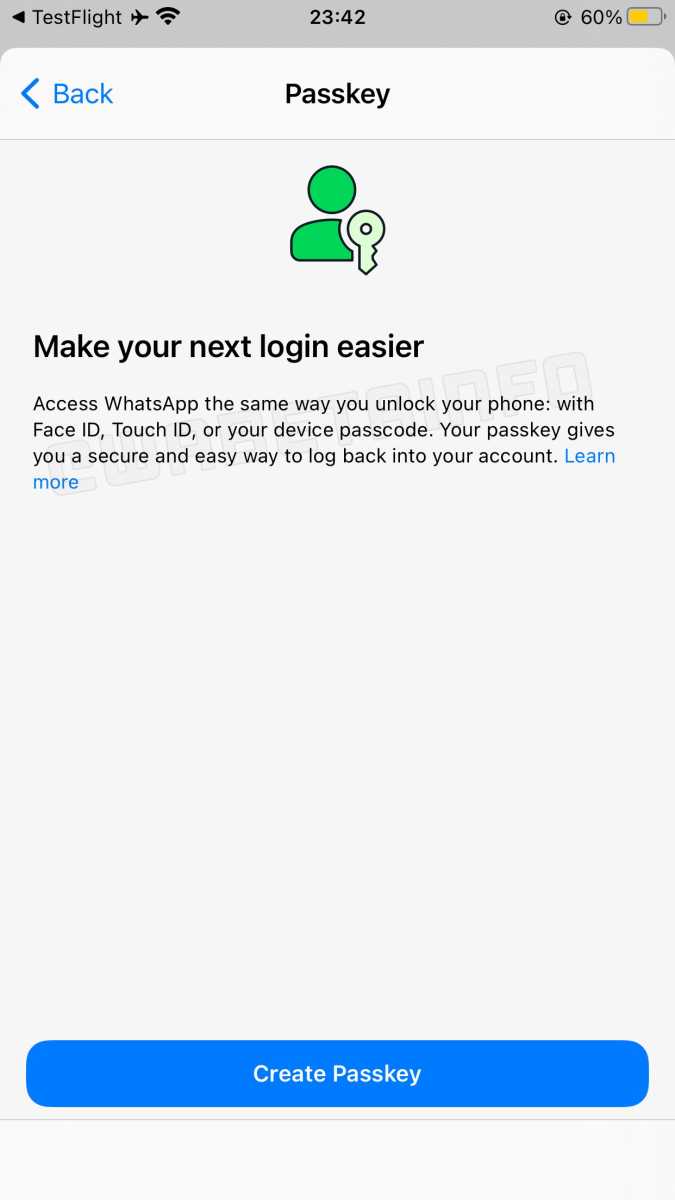 Many major services now support passkeys.
Many major services now support passkeys.
 Many major services now support passkeys.WABetainfo
Many major services now support passkeys.WABetainfo
 Many major services now support passkeys.WABetainfo
WABetainfo
Many major services now support passkeys.WABetainfo
WABetainfo
I now recommend a passkey as a primary method for login where available, so long as you’re using a system that backs them up. Apple and Android phones automatically sync passkeys across devices, as do password managers that can save passkeys. If you don’t trust the cloud, you should set up more than one hardware dongle as a passkey device. You can also leave a very strong password + 2FA on your account as a backup method of login, in case you lose your device and can’t access an alternative one with synced passkeys.
Transitioning all your accounts to more secure logins can take time—so at minimum, tackle your most sensitive accounts first, like those related to finances, taxes, and your primary email accounts.
Lock down your financial lifeThe data lost to breaches and leaks include personally identifiable information—and not just full names, birthdates, and addresses, but also social security numbers for U.S. residents, putting them at high risk for identity theft. You should consider taking the following steps to protect yourself:
- Freeze your credit
- Check your credit report
- Freeze your banking report
- Set up an IRS identity protection PIN
You can read more about each step in our full rundown of how to stay safe when your personal details can be found on the dark web, but this list summarizes the basics for U.S. residents—and can serve as topics to consider if you live elsewhere. You want to freeze your credit and banking reports so only you can open accounts in your name, review your existing credit report for any fraudulent activity, and set up an identity protection PIN with the IRS so only you can file a tax return in your name.
 Don’t let someone else steal your tax refund from you.
Don’t let someone else steal your tax refund from you.
 Don’t let someone else steal your tax refund from you.
Don’t let someone else steal your tax refund from you.PCWorld
 Don’t let someone else steal your tax refund from you.
Don’t let someone else steal your tax refund from you.PCWorld
PCWorld
If all goes smoothly, you shouldn’t need more than half an hour per step—meaning most people can tackle these over the course of a week pretty easily.
Afterward, you’ll need to keep track of PIN numbers to temporarily unfreeze your credit or banking profiles, as well as file your taxes. You can use a password manager to store these securely—if you’re concerned about someone breaching your service, you can opt for a locally stored file. (Or you can split the difference and use a database file saved to a cloud account with a major company with robust security teams, like Google, Apple, or Microsoft.)
Be careful of who you talk toAt this point, the dark web is full of personal identifiable information on most of us—meaning bad actors can easily craft personalized scams. They know not just details like your name and residence, but also websites and services you’ve signed up for.
So screen all your communication carefully—and be wary of anything full of high urgency. Maybe your package is truly about to go astray, suspicious activity has actually appeared on your credit card, or your brother really did lose his wallet on vacation. You still have time to figure out if the message is legitimate, as security experts recommend.
 Look up official contact information and initiate communication through them to verify that a message or call you’ve received is legtimate.
Look up official contact information and initiate communication through them to verify that a message or call you’ve received is legtimate.
 Look up official contact information and initiate communication through them to verify that a message or call you’ve received is legtimate.
Look up official contact information and initiate communication through them to verify that a message or call you’ve received is legtimate.PCWorld
 Look up official contact information and initiate communication through them to verify that a message or call you’ve received is legtimate.
Look up official contact information and initiate communication through them to verify that a message or call you’ve received is legtimate.PCWorld
PCWorld
For example, if your credit card has been compromised, don’t click on links in the email or text message informing you about it, or give personal information to whomever has called you. Instead, you should initiate contact with your bank using the contact info listed on your credit card or their website, and follow up through those means.
If instead you’re trying to verify communication from someone you know, rather than a corporation, the same rules apply. For phone calls, ring them back on their known line (since incoming phone numbers can be spoofed). For messages over email, text, or other communication platforms like Messenger, try a different alternative in case their account has been hacked. (Ex: If you get a request for a quick wire transfer over Messenger, try calling or texting them to confirm their account wasn’t hacked.)
In this new hellscape for digital privacy, trust no longer can be something you automatically give—especially with the rise of AI being used to create even more sophisticated scams.
Stay current with the newsAs part of avoiding personalized scams, it helps to know what further data breaches and leaks have occurred. For example, AT&T subscribers aware of the company’s loss of customer data (including social security numbers) could more carefully scrutinize communication related to their accounts.
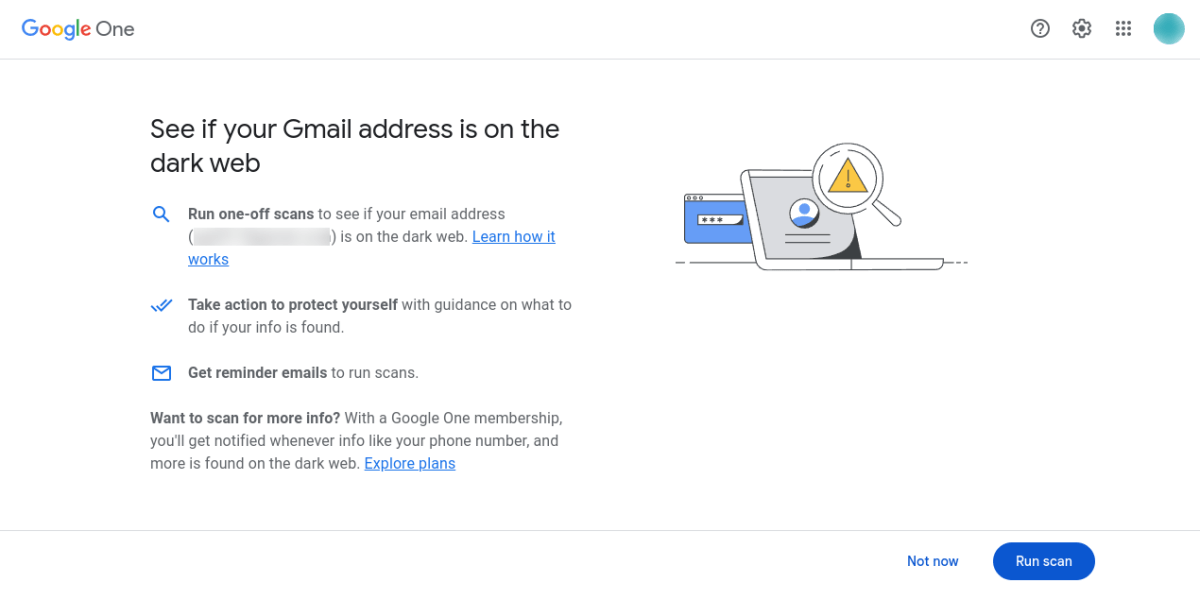 Google’s Dark Web Monitoring used to be an exclusive perk for its Google One subscribers—but the company has since made it free to all of its users.
Google’s Dark Web Monitoring used to be an exclusive perk for its Google One subscribers—but the company has since made it free to all of its users.
 Google’s Dark Web Monitoring used to be an exclusive perk for its Google One subscribers—but the company has since made it free to all of its users.
Google’s Dark Web Monitoring used to be an exclusive perk for its Google One subscribers—but the company has since made it free to all of its users.PCWorld
 Google’s Dark Web Monitoring used to be an exclusive perk for its Google One subscribers—but the company has since made it free to all of its users.
Google’s Dark Web Monitoring used to be an exclusive perk for its Google One subscribers—but the company has since made it free to all of its users.PCWorld
PCWorld
You can stay abreast of the news in several ways—and generally, you’ll want to lean on more than one source, as not ever service reports the same events, much less on the same timetable. Here are some to consider:
- Broadcast and online media (including PCWorld): These outlets generally report on huge breaches, as well as those relevant to their core audience
- Google: If you have an account, you can access the company’s Dark Web Monitoring service, which can be surprisingly quick to report new leaks or breaches
- Antivirus suites: Paid subscriptions often include Dark Web Monitoring, while free ones will sometimes report if basic information about you (email, name) has leaked
And as always, keep an eye out for email updates from the companies and services you do business with. Often email or written communication will include details about the information lost and any remedial services being offered—but you’ll want to corroborate the details with news reports to make sure the message you’ve received is trustworthy.
