Your VPN’s ‘no-log’ policy: What it is and why it matters
Connecting to a VPN server hides your traffic by rerouting it through an encrypted tunnel. Your ISP and other outside parties are no longer able to see your online activity—but the one who owns the tunnel still can. All of your data is then solely handled by a VPN provider and that’s why trusting the service to not keep any logs of your activity is imperative.
Almost every major VPN provider today will claim to have a “no-logs” policy. But what does that mean exactly, and why is it critical when choosing a VPN service? I’ll break it all down, discuss why it matters, and how to feel safer with your online privacy while using a VPN.
If you’re looking for a VPN that you can trust, all of my picks for best VPN services have been thoroughly vetted via independent no-logs audits, so you can rest assured your data will be in safe hands.
What is a no-logs policy?A VPN’s “no-logs” policy means the service does not collect—or log—any traffic that passes through its servers, such as private data including browsing history, home IP address, cookies, and files downloaded. This policy represents a VPN’s stance on data retention and commits the company to comprehensive, across-the-board user privacy measures.
The issue with no-logs claims is that it’s impossible for a user to verify that their data isn’t being collected from the outside. That’s why many top VPNs go the extra step of hiring external auditors to substantiate these claims. The very best no-logs VPNs provide as much transparency as possible, not only clearly laying out their data collection practices, but also regularly undergoing independent audits.
Of course, VPNs do need to collect some user data to make sure the service is properly maintained and running optimally. If the VPN imposes a device limit, it will need to log connection activity. To make sure that servers are not overloaded, a VPN will need to track data usage.
The key here is to make sure that all of these logs are anonymous and/or temporary. A VPN should only store your connection activity for the time you’re online and no longer. Data usage should be taken in aggregate across all users rather than user-by-user in order to fully anonymize each individual’s traffic. All of these practices should be clearly laid out in a VPN provider’s privacy policy and verified via independent audits.
Why does no-logs matter with a VPN?If you’re using a VPN it means that you are trying to gain some privacy and anonymity in one way or another. Even if you only use a VPN to get around geo-blocking restrictions with streaming services, you are still looking to hide your true identity and connection location.
Since privacy is the whole point of a VPN, it should go without saying that the VPN shouldn’t act in any way to compromise that privacy. This is where a no-logs policy comes in. It is the cornerstone of a VPN’s commitment to keeping your activity private and anonymous while connected.
Casual VPN users might not be too worried about a VPN recording your traffic, but for political dissidents, journalists, lawyers, and people under oppressive regimes, it’s a huge concern. Without sounding too hyperbolic, for those in high-risk situations, a VPN’s trustworthiness can be a matter of life or death.
Even in the worst-case event where a government were to seize control of a VPN’s servers, if the service is abiding by a no-logs policy there would be nothing for the authorities to find. This was the case in 2017 for ExpressVPN when Turkish authorities seized one of its servers while investigating a high-profile assassination. ExpressVPN’s no-logs policy was ultimately vindicated as authorities were left empty-handed.
I’m not at all saying that VPNs should be used to hide criminal activity, but they should stay true to the policies they promise.
How to check what data your VPN collects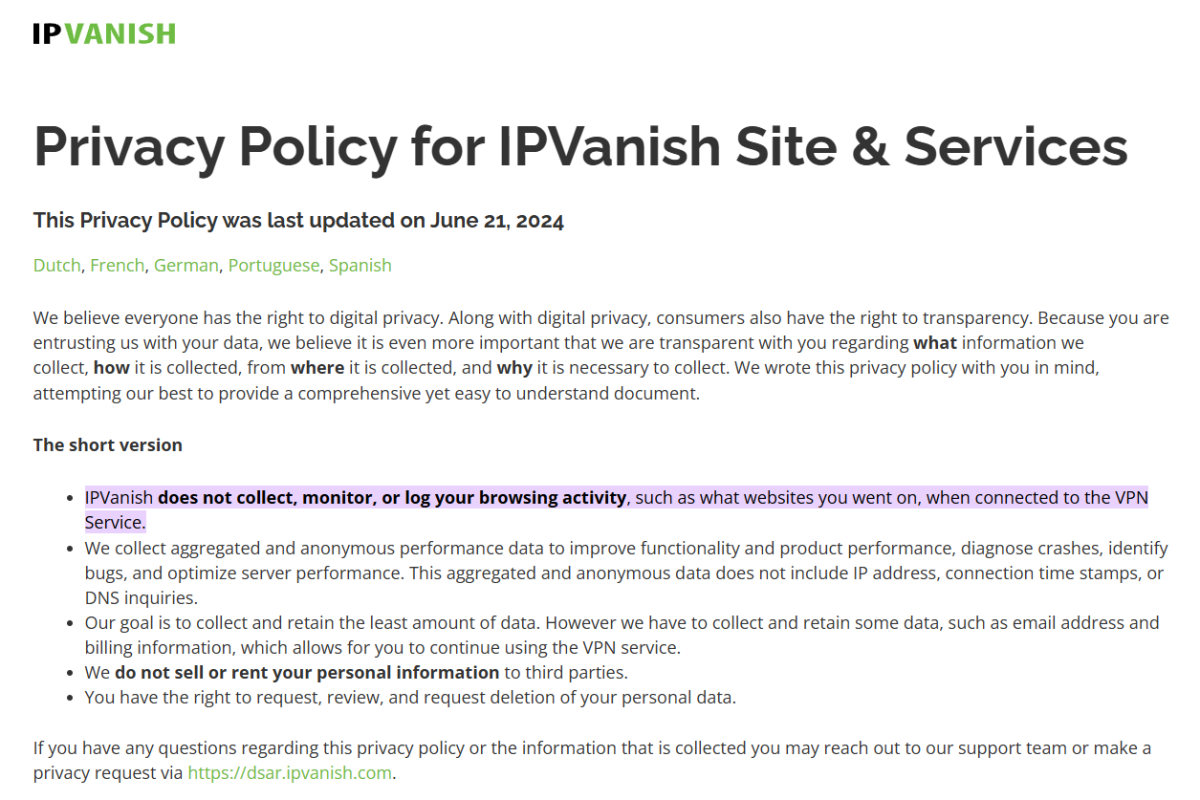
IPVanish provides a good example of what a clear and transparent privacy policy should look like.

IPVanish provides a good example of what a clear and transparent privacy policy should look like.
IPVanish

IPVanish provides a good example of what a clear and transparent privacy policy should look like.
IPVanish
IPVanish
If you’re looking to use a VPN to keep you safe online, especially when the stakes are high, then you want a service with a clear and transparent privacy policy as well as a proven no-logs track record.
For users who demand the utmost privacy from a VPN, it’s imperative that you meticulously read through the company’s privacy policy before using the service. Sometimes it can be a bit tricky to find these privacy policies through the provider’s website. Your best bet is to do a Google search for “(VPN’s name) + privacy policy” then choose the link directing you to the company’s website.
Some privacy policies can be extremely detailed and full of legal boilerplate. It might be a slog to get through, I know, but it’s worth it to find out what data is being collected. As a rule of thumb, if a company does not clearly and transparently describe the data that it does and does not collect, then you should avoid that service.
Also, be sure that the policy states how long the VPN keeps collected data. This may include connection logs and overall data usage. All of this should be either anonymized or stored for a short time only. If your VPN uses RAM-only servers your data is likely to be safer as anything collected is deleted when the servers restart.
Lastly, while a company may have a transparent privacy policy, you’ll have to take them at their word unless they can show proof of independent audits. Third-party audits of a VPN service are one of the best (and only) ways a no-logs policy can be verified. Personally, I do not use a VPN unless it has gone through at least an audit in the last year or two. Ideally, a service will go through regular, yearly or twice-a-year audits.
