The paranoid’s guide to securing your smart home
The smart home makes many things more convenient within your own four walls, but also creates a number of additional technical problems — not least with regard to the security of your own data.
The market for smart home solutions is divided into two large groups:
- One includes control systems that are permanently installed by certified tradespeople.
- The other group includes components from various manufacturers that can be easily retrofitted by non-professionals and transform simple lights or thermostats into smart devices.
With the latter devices, there are a whole range of annoyances that most users don’t think about when buying. This short guide shows firstly how you can minimize the risks before you buy, and secondly how you can find and close weak points in existing devices.
Further reading: How to keep your home network secure: Smart tricks and settings
Forced to use the cloud? Best to switch offMany manufacturers force customers to allow their devices to connect to the internet because this is the only way to control them from any location. For example, the devices from Chinese manufacturer Xiaomi (Mi Lamp and fans) can only be controlled via a smartphone app (unless you use the switches on the devices, but you don’t need a smart home for that).
Unfortunately, setting up the app and therefore using voice assistants such as Alex or Google Home is mandatory.
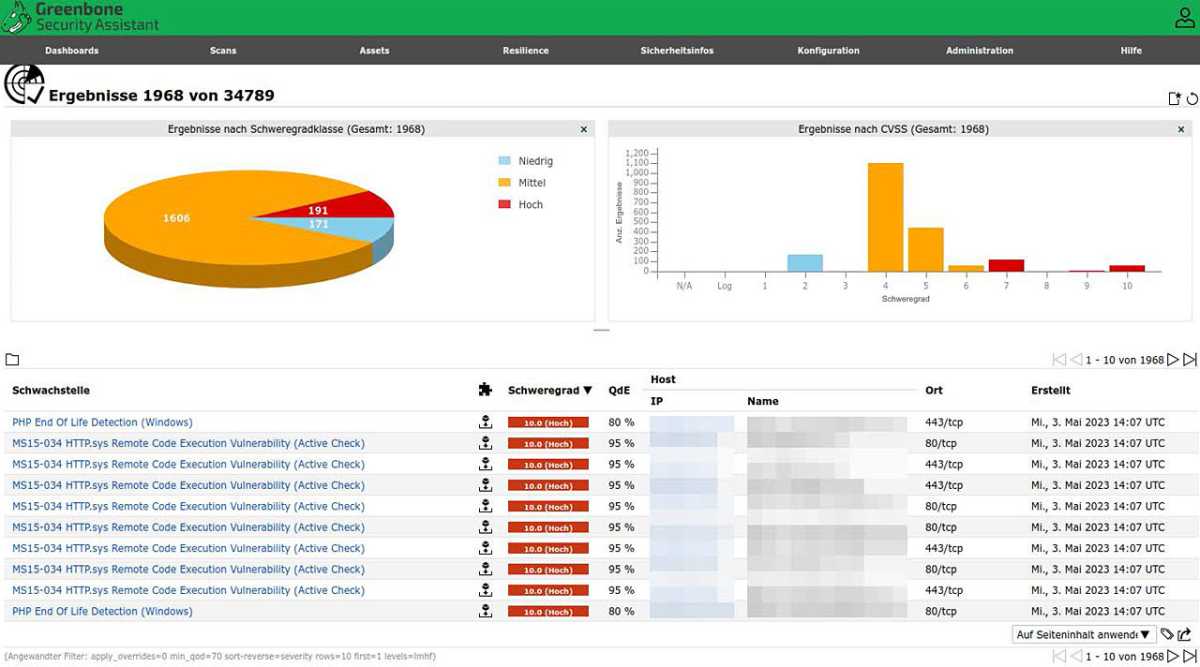
Open VAS (also included with Kali Linux) analyzes the local network and all devices for vulnerabilities and configuration errors.

Open VAS (also included with Kali Linux) analyzes the local network and all devices for vulnerabilities and configuration errors.
IDG

Open VAS (also included with Kali Linux) analyzes the local network and all devices for vulnerabilities and configuration errors.
IDG
IDG
It is therefore hardly surprising that the Shodan search engine can also be used to easily gain insights into other people’s rooms — thanks to unsecured and rarely updated webcams.
It is advisable to read the reviews before making a purchase and to pay attention to such a compulsion to use the cloud. There should be no need for this within your own four walls.
With alternative bridges such as the Raspbee or Conbee, control is also possible without the cloud (provided the device is compatible).
And you should always ask yourself whether a function is actually needed: If you’re looking for convenient temperature control for heating or ventilation, you don’t necessarily need a function that recognizes via smartphone that you are approaching the building (which can only be achieved by connecting via the internet).
When we talk about security risks here, we are not just talking about the security of the data within your own network. If hijacked devices in the network belong to a botnet, they can no longer be used, not to mention all the legal complications.
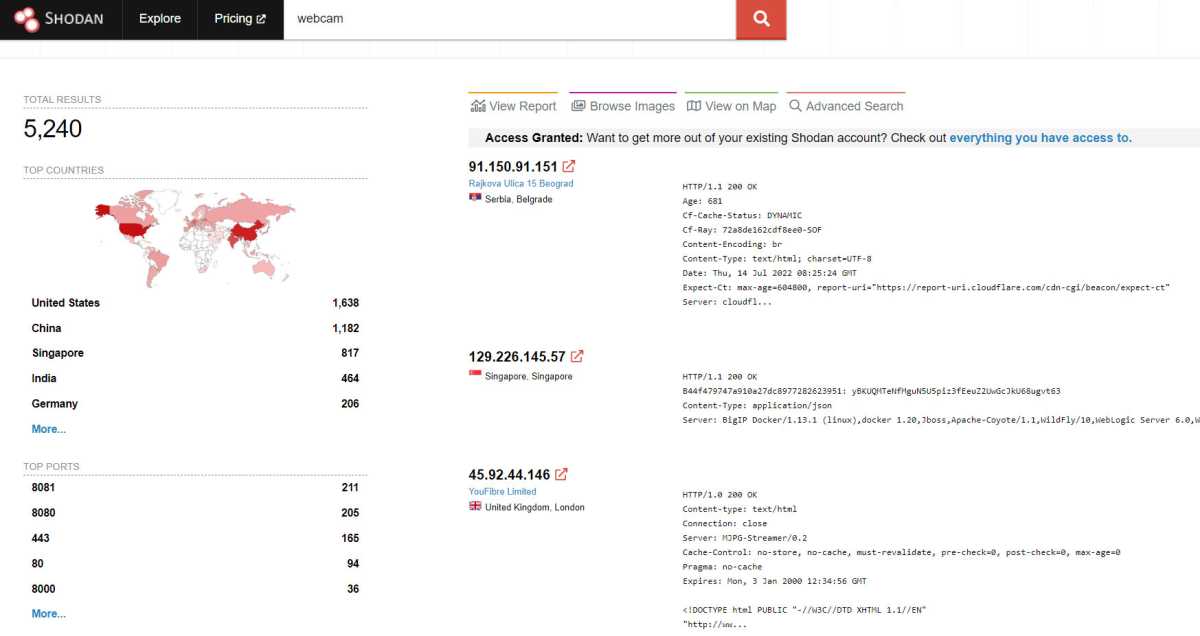
The Shodan search engine produces astonishing results. Inadequately secured webcams often allow people to look into other people’s homes.

The Shodan search engine produces astonishing results. Inadequately secured webcams often allow people to look into other people’s homes.
IDG

The Shodan search engine produces astonishing results. Inadequately secured webcams often allow people to look into other people’s homes.
IDG
IDG
Wi-Fi? A question of connectionSecurity risks can be minimized by choosing the right hardware and its connectivity. At first glance, devices that connect to Wi-Fi seem convenient. Although an app is usually required to set this up, it is only used to store the network key in the device.
However, using Wi-Fi also exposes the devices to all the attacks that attackers use against a wireless network.
In the descriptions of their devices, manufacturers only emphasize the convenience and ease of setup. References to the standard used tend to remain hidden. Devices that follow a different standard, such as Zigbee, are better than having countless devices in the house that connect to the home’s own Wi-Fi.
Tip: If it absolutely has to be Wi-Fi (because you have already purchased the lamps or radiator controls), you can isolate the components in a separate network. The Fritzbox, for example, has an additional “guest network” that can be used for these devices.
The router as a weak pointIn all efforts to achieve greater security for IoT devices within your own four walls, you should always prioritize the router. This is where the biggest vulnerabilities are usually hidden.
These include forgotten port authorizations that you created once to try something out. In addition to the port shares, also pay attention to protocols that are particularly frequently exploited by attackers. These include UPnP (Universal Plug and Play), for example.
UPnP makes it easier for devices within a network to find each other and establish connections. However, if a device (and its firmware) is allowed to set up port sharing independently, it is conceivable that this simple protocol can also be accessed externally. This is then easy prey for any bot.
The best strategy for hardening the network is to consistently start from a blacklist. Switch off all external connections to devices that are not absolutely necessary for functionality. In short: Everything that is not needed should also be switched off.
Transparency through your own platformsEvery manufacturer recommends a separate app for controlling the devices. With a large number of devices, this is anything but smart and convenient in the long run. Apple’s Homekit or Google Home and Alexa aim to rectify this, at the cost of no longer being able to take care of potential vulnerabilities.
Security-conscious users with expertise can use applications such as Open HAB, Domoticz, or iobroker to put together a customized environment that is easier to maintain, offers more transparency, and also enables cross-device processes.
Detect and close vulnerabilities
Tools such as Open VAS usually provide unique CVE numbers for vulnerabilities found, which you can then use to search for patches and possible solutions.

Tools such as Open VAS usually provide unique CVE numbers for vulnerabilities found, which you can then use to search for patches and possible solutions.
IDG

Tools such as Open VAS usually provide unique CVE numbers for vulnerabilities found, which you can then use to search for patches and possible solutions.
IDG
IDG
If you want to find out about potential vulnerabilities in the devices and systems you use, you need security solutions. Open VAS (“Open Vulnerability Assessment System”), which is available under the commercial label of the company Greenbone, is one such vulnerability scanner.
You can install it on your system via Docker or from the source code. Alternatively, you can use the well-known Kali Linux distribution, which also has the scanner on board.
Scanning takes a while, but at the end you will receive a comprehensive and graphical report to recognize existing vulnerabilities. Each vulnerability is characterized by a unique CVE number. You can then find out about possible damage and can also search for patches on the internet.
On the other hand, it is more difficult to detect possible ongoing attack attempts or anomalies in the network. On the one hand, you need a tool that scans the data packets and points out possible problems.
Secondly, knowledge of protocols and network traffic is required in order to interpret the results correctly. Under Kali Linux, for example, you can install the Suricata program, which enjoys an excellent reputation. However, the actual work only begins after installation, which is beyond the scope of this article.
