Officials have broken silence on CrowdStrike issues

Last week, a botched update from CrowdStrike issue caused millions of Windows devices to come to a screeching halt. The chaos, affecting around 8.5 million machines, stemmed from a flaw in test software.
This faulty update somehow slipped past the usual checks, leading to widespread crashes. In response, CrowdStrike has vowed to ramp up its testing and improve error handling for future updates.
Notably, this fiasco didn’t just affect CrowdStrike as it also triggered a significant outage for Microsoft, amplifying the overall disruption. The dual failures underscored just how fragile cloud services and software ecosystems can be when things go wrong.
Today, CrowdStrike issue saga continues with the following post on X from officials, followed by a blog post:
Update: Our preliminary Post Incident Review (PIR) is available at the link below. Details include the incident overview, remediation actions, and preliminary learnings. More to come in our full Root Cause Analysis (RCA).
Automated recovery techniques, coupled with strategic…
— CrowdStrike (@CrowdStrike) July 24, 2024
Can a $10 CrowdStrike gift card apology really fix the damage?
The roots of the CrowdStrike issueCrowdStrike’s Falcon software, a vital tool for businesses to guard against malware and security breaches, was at the heart of the issue. A routine update meant to collect telemetry data about potential threats instead caused catastrophic crashes. The problematic file, a small 40KB update in the Rapid Response Content, managed to evade thorough testing, leading to system-wide failures reminiscent of old-school computer viruses.
The core of the CrowdStrike issue was tied to the Rapid Response Content update, which aimed to enhance malware detection by updating the Falcon sensor.
This particular update contained faulty data that bypassed the Content Verifier due to a bug. Typically, CrowdStrike’s updates undergo both automated and manual tests.
However, this update either wasn’t subjected to the same rigorous testing or inexplicably passed, leading to widespread system crashes.
The root of the problem was a misplaced confidence in the reliability of their Content Validator. Back in March, a new deployment led CrowdStrike to believe their validation process was foolproof.
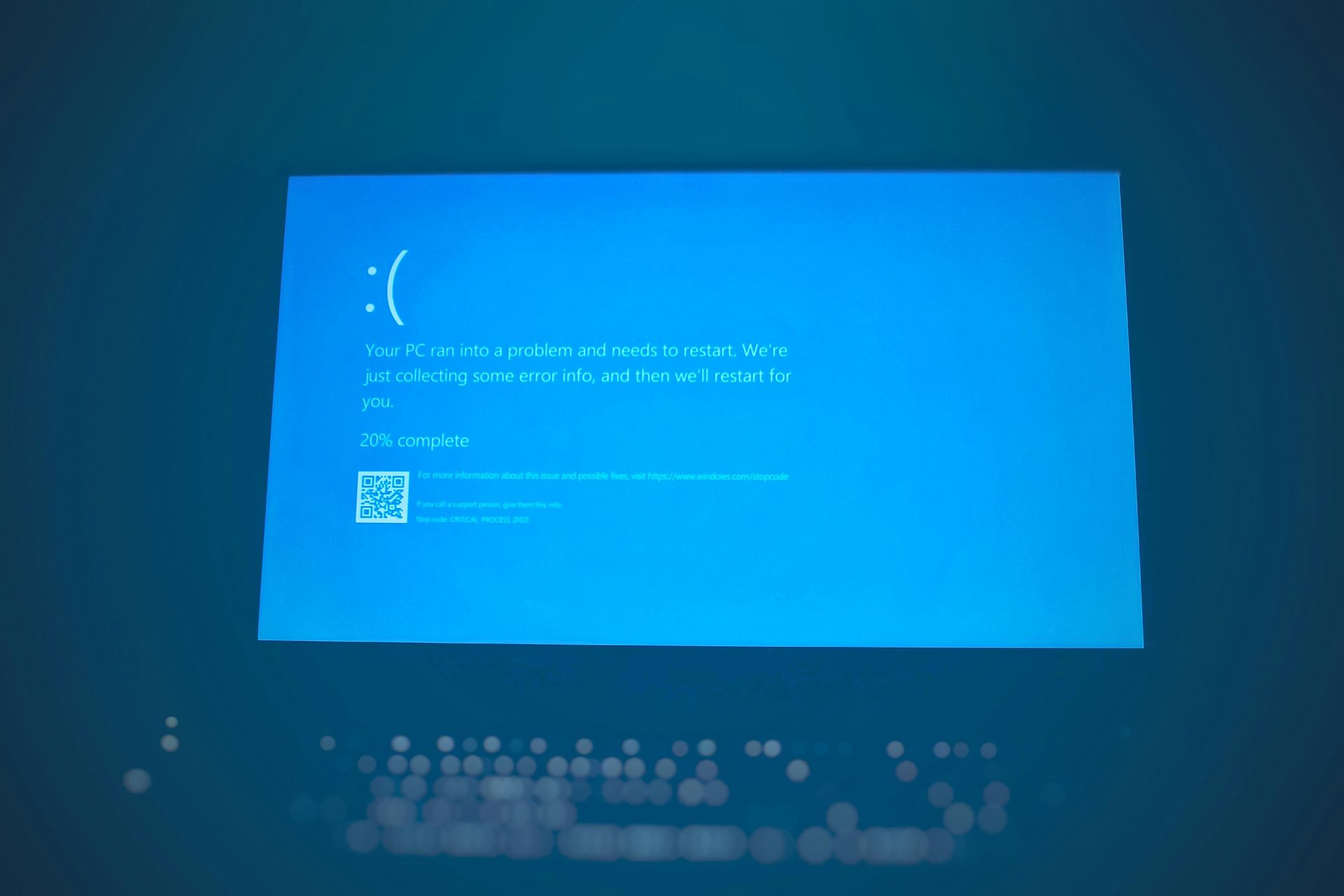 The Microsoft outage, though different in origin, occurred concurrently with the CrowdStrike issue (Image credit)
The Microsoft outage, though different in origin, occurred concurrently with the CrowdStrike issue (Image credit)
This assumption proved disastrously wrong. The faulty update triggered an out-of-bounds memory exception in the sensor’s Content Interpreter, causing Windows machines to crash with the dreaded Blue Screen of Death (BSOD).
The CrowdStrike issue erupted on a Friday, just as businesses were winding down for the weekend. The timing couldn’t have been worse, leading to immediate disruptions across numerous organizations.
The faulty update, intended to boost security, instead crippled systems, causing significant downtime and frustration.
Can a $10 CrowdStrike gift card apology really fix the damage?
How did the Microsoft outage start?The Microsoft outage was significantly affected by a buggy update from CrowdStrike. This incident highlighted the vulnerability of cloud services and how interdependent systems can amplify disruptions.
The exact cause of the Microsoft outage was different, but it occurred concurrently with the CrowdStrike issue, emphasizing the broader impact on tech infrastructure.
What is CrowdStrike outage?The CrowdStrike outage was a major disruption caused by a faulty update in CrowdStrike’s Falcon software. This update, intended to gather telemetry data about potential threats, instead led to widespread crashes of around 8.5 million Windows devices.
The incident was traced back to a flaw in the Rapid Response Content update, which managed to slip through the validation process.
When did the CrowdStrike outage start?The CrowdStrike outage began on a Friday, a particularly inopportune time as businesses were winding down for the weekend.
This timing exacerbated the impact, causing immediate disruptions across numerous organizations and leading to significant downtime and frustration.
 The problematic update which led to CrowdStrike issues intended to gather telemetry data about potential threats instead caused widespread system failures due to a flaw in the Rapid Response Content (Image credit)
What is CrowdStrike Falcon?
The problematic update which led to CrowdStrike issues intended to gather telemetry data about potential threats instead caused widespread system failures due to a flaw in the Rapid Response Content (Image credit)
What is CrowdStrike Falcon?
CrowdStrike Falcon is a cloud-based platform that provides endpoint protection for businesses. It combines antivirus, threat intelligence, and endpoint detection and response (EDR) to safeguard against malware and security breaches.
Falcon operates by deploying sensors at the kernel level in Windows machines, continuously monitoring for suspicious activity and using machine learning to enhance detection capabilities. The software’s frequent updates, like the Rapid Response Content, are crucial for maintaining protection against emerging threats.
The aftermathIn response to this debacle of the CrowdStrike issue, the company has promised several measures to prevent such a disaster from recurring. These include:
- Enhanced testing: Implementing local developer testing, content update and rollback testing, stress testing, fuzzing, and fault injection.
- Improved error handling: Enhancing the error handling capabilities of the Content Interpreter within the Falcon sensor.
- Staggered deployment: Gradually rolling out updates to larger portions of the install base instead of pushing them out all at once.
CrowdStrike Falcon, the software at the heart of this issue, is a cloud-based platform providing endpoint protection. It combines antivirus, threat intelligence, and endpoint detection and response (EDR) to safeguard against malware and security breaches, making it critical for businesses worldwide.
Falcon operates by deploying sensors at the kernel level in Windows machines. These sensors continuously monitor for suspicious activity and use machine learning to improve detection capabilities. Updates like the Rapid Response Content are crucial for maintaining protection against new threats. However, the recent incident showed the risks when these updates are not thoroughly vetted.
Featured image credit: CrowdStrike
