Hardening Windows: How to protect your computer against attacks
Microsoft has invested heavily in increasing the security of Windows. The firewall, the automatically activated antivirus program, various security functions for protection against boot viruses and much more help to ensure that hackers and malware cannot simply hijack a Windows PC.
However, there is more to this than the standard configuration. For example, various functions that pose a security risk under certain circumstances can be deactivated.
get windows 11 pro for cheap Windows 11 Pro Price When Reviewed:
199.99
Best Prices Today:
$59 at PCWorld Store – Win 11 Pro Upgrade Only |
$79.99 at PCWorld Software Store
Price When Reviewed:
199.99
Best Prices Today:
$59 at PCWorld Store – Win 11 Pro Upgrade Only |
$79.99 at PCWorld Software Store
You can also use the group policies in Windows to make it impossible for a user to change the operating system settings. In technical jargon, this is known as hardening the software.
However, this requires in-depth knowledge of Windows and its structure. This is because the relevant switches and settings are located in different places, their function is not clear at first glance, and in some cases they can only be configured via text entries on the command line.
However, there are some tools that can save you the tedious search for the advanced security settings. They offer you a security configuration that you can simply click together with the mouse. In this article, we present a selection of them.
Before using one of the tools described, it is best to set a system restore point that can undo change
s.
Before using one of the tools described, it is best to set a system restore point that can undo change
s.Foundry

Before using one of the tools described, it is best to set a system restore point that can undo change
s.Foundry
Foundry
Caution: Some of these programs have a deep impact on the operating system. To be on the safe side, you should therefore set a system restore point before using these tools.
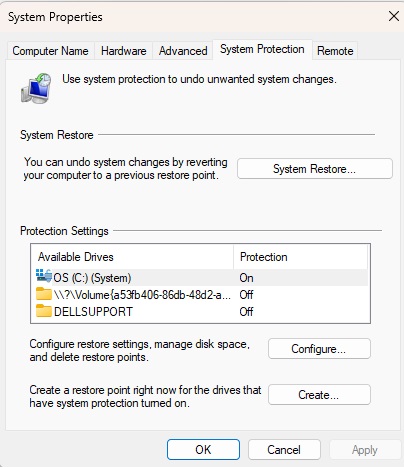
To do this, open the Windows Control Panel and go to “Restore” in the icon view. Click on “Configure System Restore” and make sure that the “System Protection” tab is open.
Select the Windows drive, click “Create,” enter a name and the current date and click “Create” again. If there are problems later, you can reconstruct the old state in the “System protection” tab via “System restore.”
Hardentools: Switch off Windows functions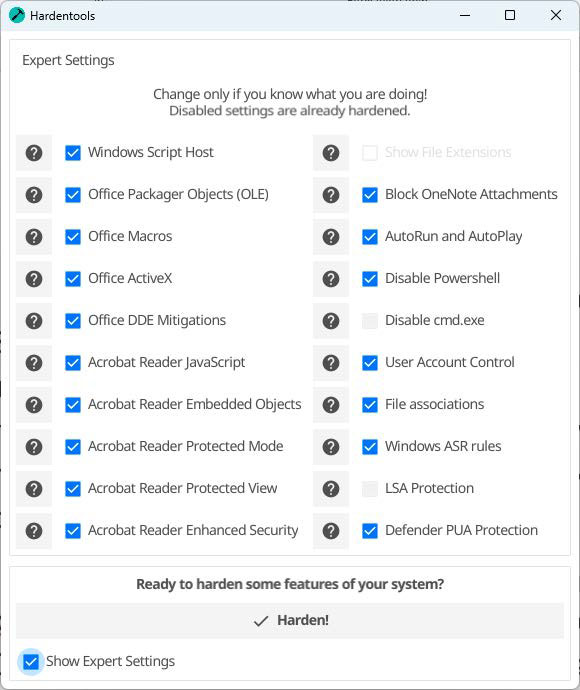
The Hardentools essentially consist of a list of Windows tweaks and options that you can use to make the operating system more secure.

The Hardentools essentially consist of a list of Windows tweaks and options that you can use to make the operating system more secure.
IDG

The Hardentools essentially consist of a list of Windows tweaks and options that you can use to make the operating system more secure.
IDG
IDG
Hardentools is an open-source program that disables a range of Windows, Office, and Adobe functions. It’s easy to use: After installation, the software recommends starting with administrator rights and then asks you to enter your Windows password.
If you tick “Show Expert Settings” on the start screen, the list of changes made by Hardentools appears. You can also prevent individual security settings there.
Otherwise, the software deactivates the execution of Powershell, the Windows Script Host, the programs in Windows Autostart and Office macros by default and ensures that the file extensions are displayed in Explorer.
Further reading: The best antivirus software 2024
It sets the Windows user account control to the highest level and only allows access after entering the Windows password.
It also activates protection against Potentially Unwanted Applications (PUA), i.e. probably unwanted programs. After calling up the program again, you can undo the changes you have made using “Restore.”
Riot Isolator: Prevent hacker activities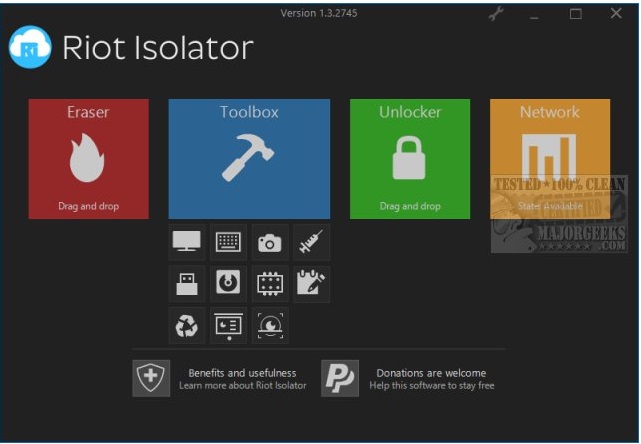
Riot Isolator blocks a number of Windows functions that are often used by criminal hackers for their attacks.

Riot Isolator blocks a number of Windows functions that are often used by criminal hackers for their attacks.
Major Geeks

Riot Isolator blocks a number of Windows functions that are often used by criminal hackers for their attacks.
Major Geeks
Major Geeks
The Riot Isolator combines a range of functions with which you can prevent the execution of known hacker techniques.
For example, the program includes a tool called “Anti-Screen Capture,” which turns every screenshot into a black area. The “Anti-Keylogger” and “Anti-Web Camera” functions prevent the recording of keystrokes and webcam images.
The “Anti-Exploit” module ensures that Windows displays the real file types. According to the manufacturer, it also recognizes the execution of processes in RAM and via the Address Resolution Protocol (ARP) and blocks them. A “removable disc protection” blocks access to USB sticks and drives.
After that, things get more martial: A “drive destroyer” deletes the hard disk and SSD drives on request, while a “RAM destroyer” does the same with the contents of the RAM. The Riot Isolator can also wipe individual files from the hard drive without leaving any residue.
The “recycle bin cleaner” is more harmless. The functions of Riot Isolator are partially identical to those of anti-virus tools. Otherwise, the software is a good addition to these programs.
Ultra Virus Killer: Immunize Windows
Ultra Virus Killer is just called that. In fact, the tool is a collection of auxiliary tools for Windows maintenance.

Ultra Virus Killer is just called that. In fact, the tool is a collection of auxiliary tools for Windows maintenance.
IDG

Ultra Virus Killer is just called that. In fact, the tool is a collection of auxiliary tools for Windows maintenance.
IDG
IDG
The name of this software is misleading. The Ultra Virus Killer does not even have an antivirus module, but is only able to automatically upload files to the Google service Virustotal and have them scanned there.
Otherwise, the software harbors numerous Windows maintenance functions under its surface. These include an autostart and service manager, a collection of Windows tweaks, and a module for deleting files and folders.
Of interest in the context of this article is “System Immunization,” with which you can protect selected files, drivers, browser components and registry entries from changes.
This should make it much more difficult for malware to nest in your Windows system. This is linked to functions for backing up and restoring the registry database.
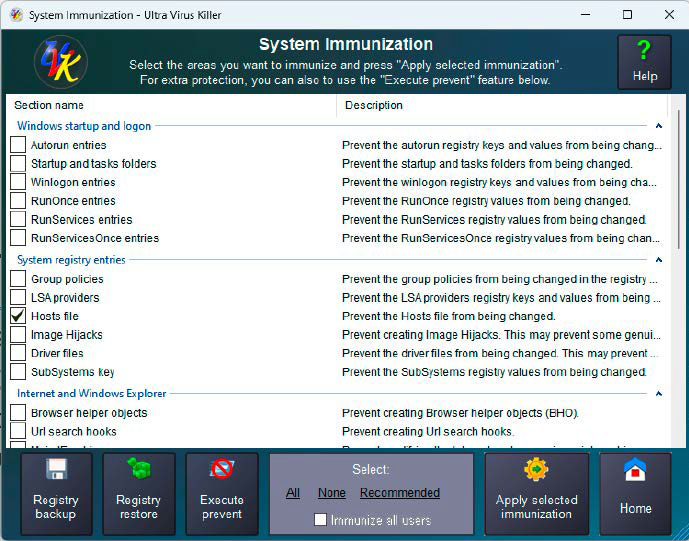
Ultra Virus Killer’s “System Immunization” allows you to protect the hosts file from editing, among other things.

Ultra Virus Killer’s “System Immunization” allows you to protect the hosts file from editing, among other things.
IDG

Ultra Virus Killer’s “System Immunization” allows you to protect the hosts file from editing, among other things.
IDG
IDG
OS Armor: Block system functionsThe OS Armor program is very similar to the Windows group policy editor. It provides a list of dozens of options that you could also define via Group Policy, but which are much easier to configure here.
For example, you can block the execution of a number of applications that work close to the system. These include the system configuration msconfig, the Ps tools from the Sysinternals Suite, the Windows terminal, the registry editor, but also third-party programs such as Teamviewer or the Nirsoft tools.
Even access to individual command line commands such as netsh.exe or diskpart.exe can be switched off.
OS Armor offers a simply designed interface, on which the program’s “Configurator” is essentially of interest.

OS Armor offers a simply designed interface, on which the program’s “Configurator” is essentially of interest.
IDG

OS Armor offers a simply designed interface, on which the program’s “Configurator” is essentially of interest.
IDG
IDG
OS Armor opens with a standard configuration that offers basic protection against manipulation by malware or other persons. The program sounds an alarm if such attempts are made. You can set up password protection in OS Armor so that nobody but you can change the settings.
Winoptimizer Free: Lock Windows functionsWinoptimizer from Ashampoo is a powerful program for tidying up Windows and making the operating system faster and more secure. It also includes a module that allows you to block individual security-relevant functions in the hardware, Explorer, and Control Panel.
Further reading: 6 ways hackers sidestep your two-factor authentication
You can find this module under “All modules – Restrict user rights.” There, in the “Hardware” section, you can, for example, deactivate the Windows CD burning function and access to other workgroup computers.
Under “Explorer,” you can switch off access to the “File” menu and the “Manage” option in the context menu of the My Computer icon.
In “Control Panel,” the Winoptimizer offers a block on changes to the desktop functionality, under “Applications” you can prevent the Windows Task Manager and other freely definable third-party applications from being called.
At the bottom of the window, you can set whether the restrictions should only apply to the logged-in user or to all users. A restart is required for the changes to take effect.
Hard Configurator: Block dangerous actions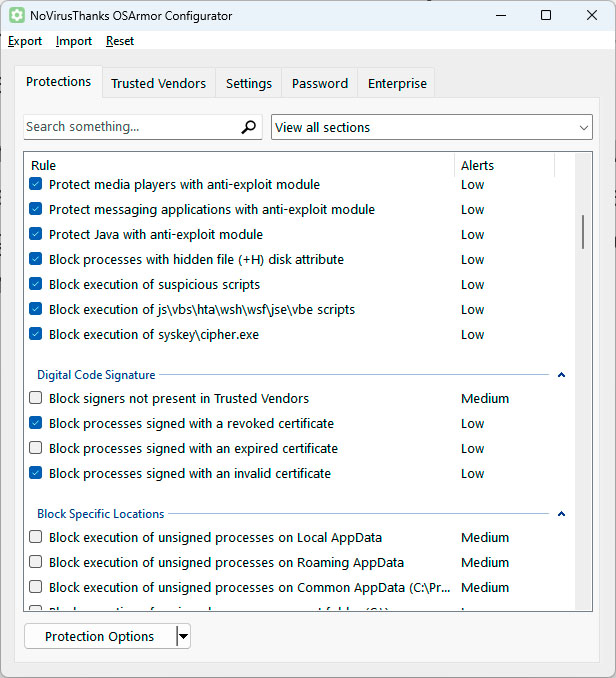
OS Armor’s “Configurator” contains a long list of tweaks and options with which you can protect the components of Windows from changes and attacks.

OS Armor’s “Configurator” contains a long list of tweaks and options with which you can protect the components of Windows from changes and attacks.
IDG

OS Armor’s “Configurator” contains a long list of tweaks and options with which you can protect the components of Windows from changes and attacks.
IDG
IDG
You only understand how the Hard Configurator works at second glance. The small tool works with an unconventional interface that only gradually reveals itself.
The two wide columns in the center are important as they list the available functions. To the left and right of this you can see the current setting. There you can, for example, block Powershell scripts or access to certain file types. Use “Apply Changes” to transfer your configuration to Windows.
Use the “ConfigureDefender” and “FirewallHardening” buttons to start modules for configuring Windows Defender and the firewall. Click on “Tools” to access additional functions for logging events in Windows, restoring the default configuration, and uninstalling Hard Configurator.
