Don’t fall for it: Hackers use Facebook ads to target you

Throughout 2024, a disturbing trend has emerged as hackers exploit Facebook ads to distribute fake Chrome extensions masquerading as legitimate password managers like Bitwarden. This sophisticated malvertising campaign preys on users’ fears of cyber threats and deceives them into downloading malicious software.
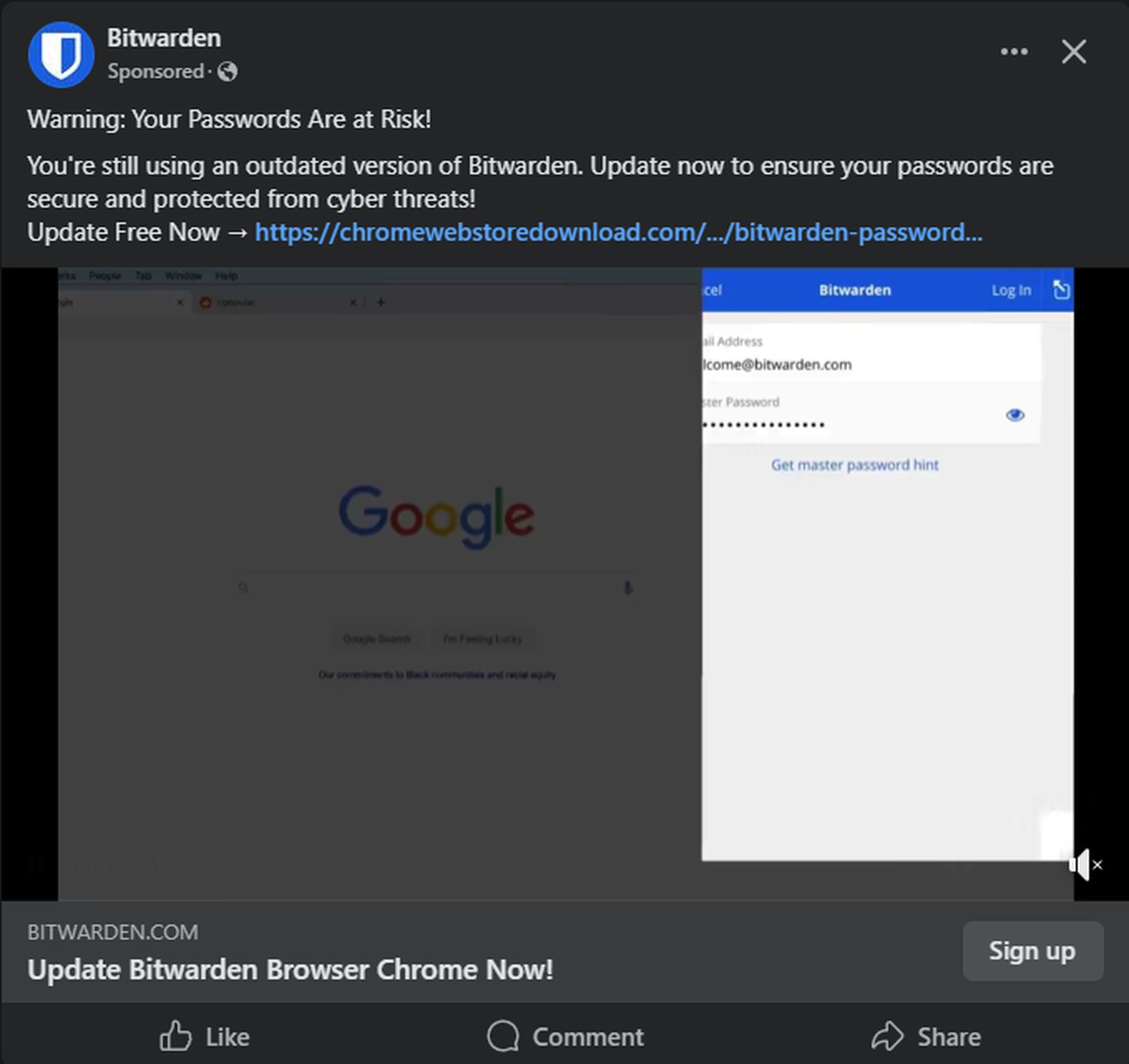
Hackers exploit Facebook ads to distribute fake Chrome extensionsBitdefender Labs has closely followed these campaigns, revealing that the latest operation was launched on November 3, 2024. Targeting users aged 18 to 65 across Europe, the attackers create a sense of urgency by claiming that users must install a critical security update. By impersonating a trusted brand, they effectively leverage Facebook’s advertising platform to gain users’ trust.
The deceptive process begins when users encounter a Facebook ad that warns them their passwords are at risk. Clicking the ad directs them to a fraudulent webpage designed to mimic the official Chrome Web Store. However, instead of a safe download, users are redirected to a Google Drive link hosting a ZIP file containing the harmful extension. To install it, users must follow a detailed process that involves enabling Developer Mode on their browser and sideloading the extension, a method that circumvents standard security protocols.
How the fake Bitwarden extension operatesOnce the malicious extension is installed, it requests extensive permissions allowing it to intercept and manipulate user activity online. As outlined in the extension’s manifest file, it operates across all websites and can access storage, cookies, and network requests. This provides hackers full access to sensitive information. For instance, the permissions include:
- contextMenus
- storage
- cookies
- tabs
- declarativeNetRequest
 Once the malicious extension is installed, it requests extensive permissions allowing it to intercept and manipulate user activity online (Image credit)
Once the malicious extension is installed, it requests extensive permissions allowing it to intercept and manipulate user activity online (Image credit)
The extension’s background script initiates a series of harmful activities as soon as it is installed. It routinely checks for Facebook cookies and retrieves vital user data, including personal identifiers and payment information associated with Facebook ad accounts. The sensitivity of the stolen data can lead to severe repercussions, including identity theft and unauthorized access to financial accounts.
Hack Microsoft win $4 million with Zero Day Quest
The use of legitimate platforms like Facebook and Google Drive obscures the malware’s true nature. Security experts recommend several strategies to mitigate risks associated with this threat:
- Verify extension updates through official browser stores rather than clicking on ads.
- Exercise caution with sponsored ads, especially those that prompt immediate updates for security tools.
- Review extension permissions critically before installation.
- Utilize security features, such as disabling Developer Mode when not in use.
- Promptly report suspicious ads to social media platforms.
- Implement a reliable security solution that detects and blocks phishing attempts and unauthorized extensions.
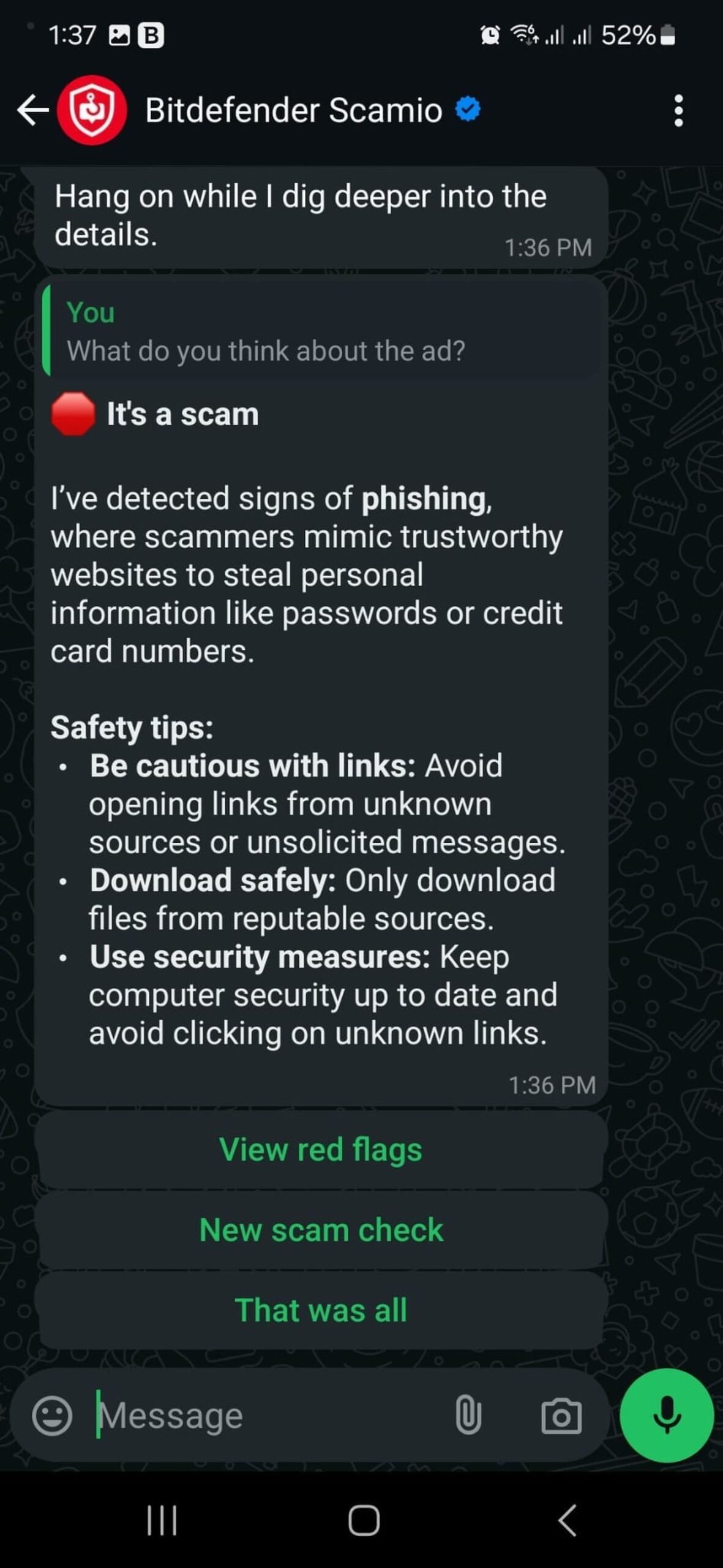 Scamio interface (Image credit)
Scamio interface (Image credit)
Bitdefender offers a tool called Scamio, which helps users identify malicious content online. It assesses links, messages, and other digital interactions to highlight potential scams, giving users an extra layer of defense.
Featured image credit: Soumil Kumar/Unsplash
