6 ways hackers sidestep your two-factor authentication
Protecting an account with just a username and password is not very smart. Both can be stolen, guessed, or cracked too easily. This is why two-factor authentication (2FA) is recommended for all important access points. It has even been mandatory for online banking for years.
With 2FA, two factors are used to gain access to an account, a network or an application. One factor is a security feature that can come from three categories:
- Knowledge (password, PIN)
- Possession (smartphone, Fido2 stick, etc.)
- Biometrics (fingerprint, facial recognition, etc.)
For 2FA to provide good protection, the two factors used must come from two different categories. If more than two factors are used, this is referred to as multi-factor authentication.
Also interesting: The Amazon triangle scam: What it is, how it works, and what to do
2FA is very secure, but not invulnerable. There are tricks and loopholes that hackers can exploit to take over an account.
This authentication app provides the corresponding one-time password for registered services. It is only valid for a few seconds before the app issues a new one.

This authentication app provides the corresponding one-time password for registered services. It is only valid for a few seconds before the app issues a new one.
IDG

This authentication app provides the corresponding one-time password for registered services. It is only valid for a few seconds before the app issues a new one.
IDG
IDG
1. The man in the middle: 2FA theft through phishingThe connection between the user and the online account is actually protected by the secure TLS (Transport Layer Security) connection. Technical procedures are designed to ensure that nobody can hack into this connection. Nevertheless, attackers can use various tricks to get between the user and their account. These are known as “man in the middle” attacks. These come in different varieties.
Phishing pages: One of the biggest threats to 2FA are phishing attacks. Cyber criminals use fake websites to trick users into revealing their login details. Victims are often lured to these phishing sites via emails, SMS, or Whatsapp messages that claim to be from legitimate companies.
Simple phishing pages “only” steal a user’s log-in data. In a man-in-the-middle attack, the website also intercepts the code for two-factor authentication. The attacker then uses the data to log in to the relevant service immediately afterwards. However, this is time-critical, as a one-time password is usually only valid for a few seconds.
The attack is correspondingly time-consuming, as the attacker must be ready when a potential victim enters their data on the fake site in order to log in themselves. However, as such attacks can often be used to steal money directly, criminals are always trying to use this method.
Further reading: Quishing and vishing: How to protect yourself from new security threats
2. Man in the browser: Malware as a man in the middleA variant of the “man in the middle” technique uses malware that embeds itself directly in the victim’s browser. The malicious code waits until the user has logged in to their bank, including 2FA, and then manipulates a transfer from the victim in the background. Examples of such malware are Carberp, Emotet, Spyeye, and Zeus.
The correct details of the amount and recipient of a transfer appear in the user’s browser. They therefore confirm them with a one-time password. In reality, however, the malware has secretly sent a different recipient and a large amount as a transfer to the bank.
How to protect yourself: Almost all banks will send you the transfer amount again for checking when requesting the one-time password for authorization. In most cases, the IBAN of the recipient is also transmitted in full or in part. Always check this data very carefully.
Further reading: Change these 5 Windows settings to improve your data privacy
3. Personal contact: You are being tricked out of your codeIn many cases, the attackers already know the username and password of an online account because they have obtained this data from a password collection on the darknet. Or they have smuggled an info stealer, i.e. malware, onto the victim’s PC.
What the attackers still need to log into the victim’s online account is the second factor. They obtain this by calling the victim. They pretend to be an employee of the bank and claim, for example, that they want to introduce a new security procedure. To do this, they claim to need authorization using the customer’s 2FA procedure.
If the victim authorizes an action via 2FA at this moment, then they have not agreed to a new security procedure but have transferred their money to the attackers’ account.
How to protect yourself: Never pass on 2FA codes and authorizations to other people or give them out on the instructions of a caller. Genuine service employees will never ask you for such secret information.
Tips for two-factor protected login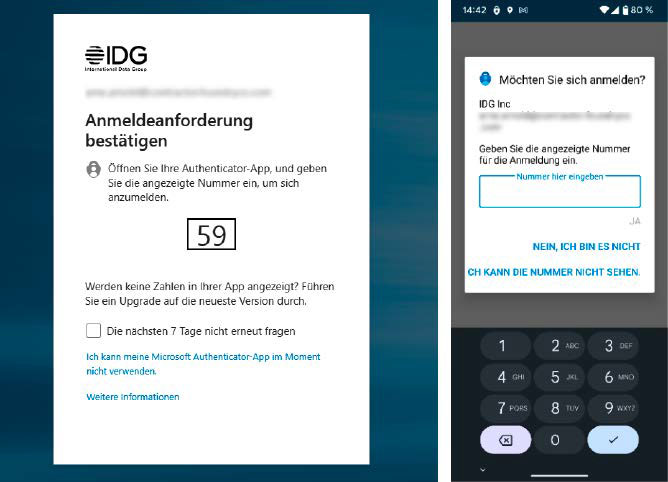
Here, a website (left) sends a push notification to the associated app on the smartphone. There, the user must now enter the displayed number to log into their account.

Here, a website (left) sends a push notification to the associated app on the smartphone. There, the user must now enter the displayed number to log into their account.
IDG

Here, a website (left) sends a push notification to the associated app on the smartphone. There, the user must now enter the displayed number to log into their account.
IDG
IDG
These tips will make logging in to a service with two-factor authentication easier and more secure.
- Create emergency codes, print them out and keep them in a safe place. You should always carry two or three of these codes with you when you are travelling.
- Activate more than one 2FA method. For example, use an authentication app and also a hardware token. This way you have a backup in case neither the app nor the emergency codes are on hand.
- You should not use 2FA codes via SMS for sensitive accounts. This is because criminals can steal the SIM card or obtain the SMS codes through phishing.
- Use an authentication app with a backup function. Then you can take the app including all codes with you to a new smartphone. Otherwise, all 2FA services will have to be set up again if you reinstall the app.
For a while, one-time passwords that a user receives by text message from their online account were considered a secure method for two-factor login. But then criminals developed SIM swapping and emptied numerous online accounts, including several million from 2FA-protected online bitcoin exchanges. Here, too, the prerequisite is that the attacker already knows the victim’s username and password.
In SIM swapping, also known as SIM hijacking, the attacker takes control of the victim’s mobile phone number. The attacker causes the mobile phone provider to send them a new SIM card or eSIM. The attacker activates this on their own mobile phone and receives the text message with the one-time password for the two-factor login.
Attackers often simply tell the mobile phone provider that they have lost their mobile phone and request a new SIM card. This should be sent to a new address. If the mobile phone provider does not want this, the perpetrators can wait until the post arrives at the victim’s correct address and empty the letterbox before the actual recipient.
This is of course very time-consuming for the attackers. However, for victims who have a lot of money in their account, it is obviously worth the effort for the criminals.
How to protect yourself: If possible, do not use SMS for 2FA. One-time codes, for example from an authentication app, are more secure.
5. Malware steals authentication cookiesMany services with two-factor login offer you the option of memorizing the internet browser on your PC. You then only have to log in once with this browser on this PC using the second factor. The next time you log in, you either don’t need any login details or just your user name and password.
This increases convenience enormously — but increases the attack surface. With this method, the service saves an authentication cookie on your PC. This contains your login data in encrypted form. If attackers succeed in placing an info stealer, i.e. malware, on your PC, they can steal the cookie with the login information. The attacker uses the cookie on their own PC to open the online service without requiring a login or a second factor.
One example of such an info stealer is Lumma, which has been attacking PCs since 2022 and is offered in Russian-language underground forums as “malware as a service.”
How to protect yourself: Of course, a good antivirus program should be installed on every Windows computer. This should block the Info Stealer. In addition, you can use your accounts with two-factor login so that you have to enter the second factor every time you log in. This is usually the default setting.
Further reading: Google’s dark web monitoring is actually pretty helpful
6. Insecure factors as an alternative when logging inA common mistake with 2FA is choosing an insecure second factor (see box “Overview of two-factor authentication”). Many users still use SMS as a second factor, even though their online service already offers better 2FA methods. However, SMS as a second factor is vulnerable to attacks such as SIM swapping (see above).
Email as a second factor is also only recommended to a limited extent. Unless you have protected your email inbox yourself with a secure two-factor login.
Weak factors are also dangerous if you only use them as a backup. Many online services offer the option of storing several login factors in one account. This is also useful as you can switch to another factor if something does not work.
However, an attacker can also fall back on one of the other login options at any time. Once again, the adage applies: A chain is only as strong as its weakest link.
So if you not only protect an account with the one-time password from your authentication app, but also activate a one-time password by email as a login option, an attacker can also use this.
How to protect yourself: It is a good idea to store several factors for logging in to your services, for example one-time passwords from the authentication app and passkeys. However, avoid insecure factors such as SMS and email (see box “Overview of two-factor authentication”).
Overview of two-factor authenticationThere are secure and less secure methods for logging in with two factors.
1. One-time passwordsSMS-based OTPs: A one-time password (OTP) is sent to the user’s mobile phone via SMS.
Security: SMS OTPs are relatively insecure as they are vulnerable to SIM swapping attacks and man-in-the-middle attacks.
App-based OTPs: A one-time password is generated by an authentication app such as Google Authenticator or Aegis Authenticator.
Security: App-based OTPs are more secure than SMS OTPs as they are not sent via external networks. However, they are susceptible to phishing attacks.
Email-based OTPs: A one-time password is sent to the user by email.
Security: Email OTPs are less secure than other methods as emails can be intercepted and are often sent over less secure networks. In addition, email accounts are often the target of phishing attacks.
Push notifications: A push notification is sent to an authentication application (such as Microsoft Authenticator) on the user’s mobile phone. The user must agree to the notification.
Security: Push notifications are relatively secure as they require direct interaction from the user. However, they are vulnerable to social engineering attacks where the user is tricked into confirming the notification.
2. Hardware tokensU2F/FIDO2 tokens: USB or NFC-based hardware tokens (for example Yubikey) based on the U2F/FIDO2 standards.
Security: These tokens offer a very high level of security as they use cryptographic keys for authentication and are resistant to phishing and man-in-the-middle attacks.

Hardware tokens as a second factor for logging in offer a high level of security and also work on smartphones.

Hardware tokens as a second factor for logging in offer a high level of security and also work on smartphones.
IDG

Hardware tokens as a second factor for logging in offer a high level of security and also work on smartphones.
IDG
IDG
3. PasskeysPasskeys: Passkeys are used by most services as an additional option to passwords.
Security: If the passkey is set up as a real second factor, the login is very secure. However, as an alternative to a password, passkeys offer little more protection than a password, as you can switch to password login.
4. BiometricsFingerprint, etc: Fingerprint sensors or a biometric camera are used to unlock or log in.
Security: Fingerprints are easier to falsify than many people think, at least when in direct contact with the victim.
Security assessment and recommendationsHighest security: Hardware tokens offer the highest security due to their physical nature.
Medium security: Passkeys, app-based OTPs, push notifications, and biometrics are more secure than SMS and email OTPs, but are vulnerable to attacks such as social engineering.
Least secure: SMS and email OTPs are the most vulnerable to attacks and should be avoided.
