The State of Web3 Security in 2024
Challenges, innovations, and the path forward
 Table of Content
Table of Content- The Current Battlefield
- Breaking Down 2024’s $2B Losses in Web3
- Top Attack Vectors Explained
2. Security Evolution
- Landmark Hacks That Changed Everything
- Web2 vs Web3: Learning From History
3. The New Defense Playbook
- Beyond Basic Audits
- Smart Contract Security Today
- The Rise of Embedded Security
4. Building Better
- Solving the Trust Paradox
- Securing the Path to Mass Adoption
Read time: 15 minutes
IntroductionThe crypto industry has the power to change the world, but it also faces a paradox: its promise of being decentralized relies on trustless systems, but security breaches highlight how fragile trust can be in practice.
As more people use crypto, security can no longer be just an afterthought: it needs to be part of the infrastructure. We need to increase the credibility of our industry in the public eye, to do this, we need Credible Security. Security that is embedded and verifiable.
This article delves into the changing landscape of crypto security, examining vulnerabilities, trends, and the proactive measures required to protect the decentralized future.
Security LandscapeIn the first quarter of 2024, a total of $826,205,224 was lost across 67 attacks. The following quarter, hackers stole $512,928,000, and this quarter, $463,594,618. Notably, this quarter’s return of only 4.1% of stolen funds, compared to last quarter’s 14.4%, significantly increased the loss.
This makes almost $2 billion worth of assets stolen so far this year. This shift indicates that attacks were, on average, more substantial.
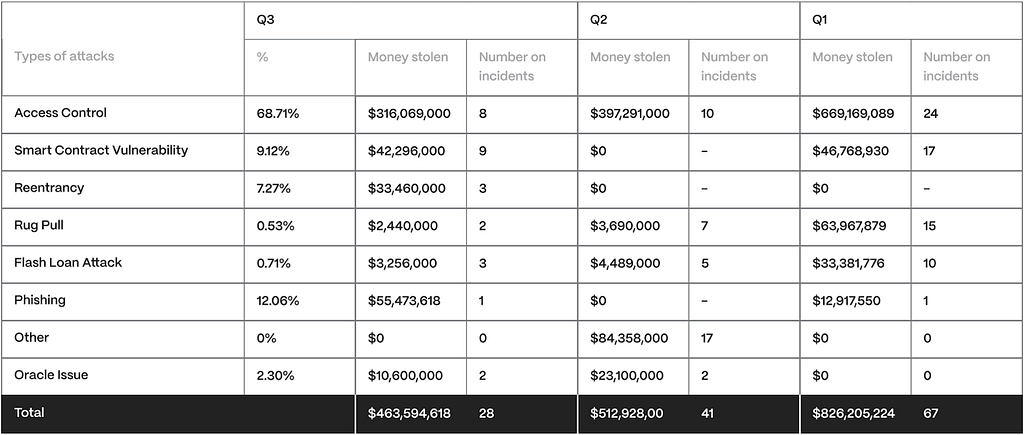 Fig. 1: Asset Stolen has steadily decreased throughout the year
Fig. 1: Asset Stolen has steadily decreased throughout the yearHowever, this quarter represents the lowest amount of recovered or frozen funds in recent memory. Out of all the victims, only three projects were successful in recovering a total of $23.5 million in lost assets. Like in previous quarters, we had hoped that the practice of returning a portion of the stolen funds would continue, but alas!
This trajectory reveals two critical insights:
- The average magnitude of successful attacks has increased, despite a decrease in total incident count
- The recovery rate of stolen funds has dropped to a concerning 4.1% in Q3, down from 14.4% in Q2
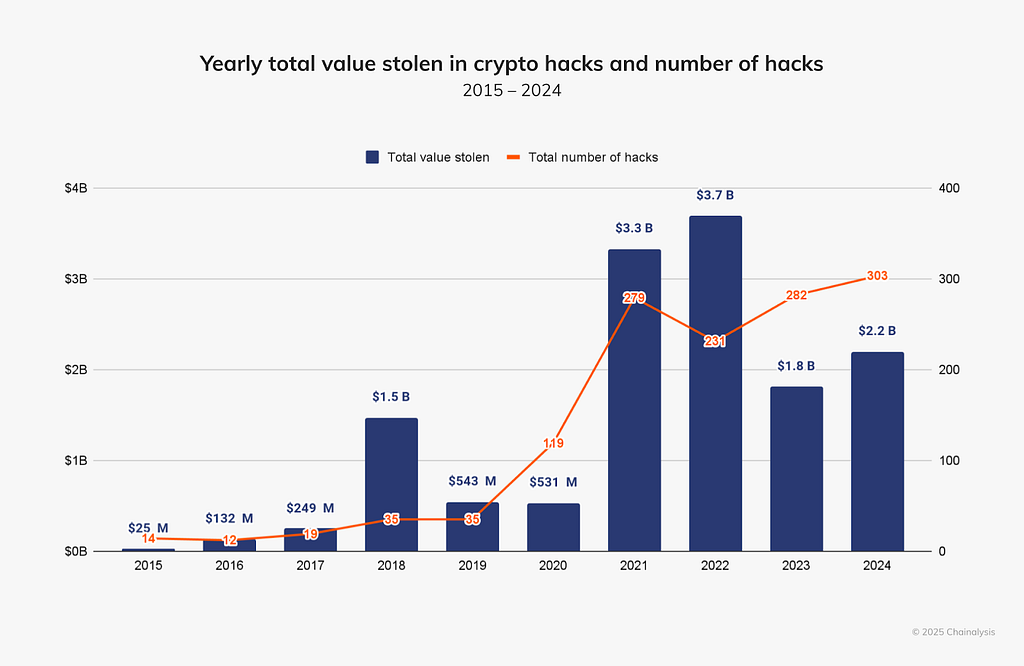 Fig. 2: Year-wise total number of hacks vs amount stolen
Fig. 2: Year-wise total number of hacks vs amount stolenAs shown in the chart above, in 2024, stolen funds grew by 21.07% YoY to $2.2 billion, with hacking incidents rising from 282 in 2023 to 303 in 2024.
Apart from that, the ecosystem was on pace to match the $3 billion+ records of 2021 and 2022 by the end of July. However, growth slowed significantly after July and has since leveled off.
Phishing was the most costly attack vector in Q3 of 2024, with $343,099,650 stolen across 65 incidents. Private key compromises were the second most costly attack vector in Q3 2024, with $324 million stolen across 10 incidents. In total, these top two attack vectors accounted for a total of $668 million stolen.
This quarter also saw code vulnerabilities, reentrancy events, and price manipulation attacks that stood out. In 44 incidents, code vulnerabilities led to the theft of $39,680,651, while reentrancy came in second with $30,353,579 stolen.
Ethereum has been the target of 86 hacks, totaling $387 million.
The Evolution of Crypto SecurityFixing Crypto security flaws has been challenging and has cost more than $14 billion in the last five years. The number of hacks that happen each year is going down, but the damage they do is still big and costs a lot of money. This trend shows that Crypto security is still very new compared to the more established Web2 security standards.
Pivotal incidents that shaped crypto security- The DAO hack (2016), the first major smart contract vulnerability, caused over $50 million in losses and prompted the industry to adopt code audits and governance reforms.
- Parity Multisig Hack (2017), a critical vulnerability in the Parity Multisig Wallet (v1.5+), allowed an attacker to exploit the initWallet function and reinitialize wallet ownership. The attacker took control of the wallet and stole over 150,000 ETH by forwarding unmatched function calls using delegateCall. This incident highlighted the risks of poorly secured library patterns, the need for stricter access control, and a safer smart contract architecture.
- The Ronin network hack (2022) resulted in a $625 million loss due to the compromise of the network’s multisig validator mechanism, where attackers gained control of five out of nine validators.
- Euler Finance (2023), an advanced flash loan attack that resulted in $196 million in losses, showed how sophisticated attackers were becoming.
- The DMM bitcoin exploit (2024), which resulted in a $305 million loss due to access control issues, exposed the shortcomings of the current security measures.
These incidents have pushed for stronger security measures like multi-signature wallets, bug bounty programs, and competitive auditing. However, as decentralized applications (dApps) grow more complex, new vulnerabilities arise, making preventive security measures essential.
Dominant Threats in the Crypto LandscapeCrypto has faced persistent threats since its inception, and many of the early attack vectors are still relevant today. Exploits like stolen private keys, broken access controls, flash loan attacks, price oracle manipulation, and misconfigurations still remain major vulnerabilities in the ecosystem.
These flaws are frequently caused by a combination of poor privilege management, flawed contract logic, and insufficient testing procedures.
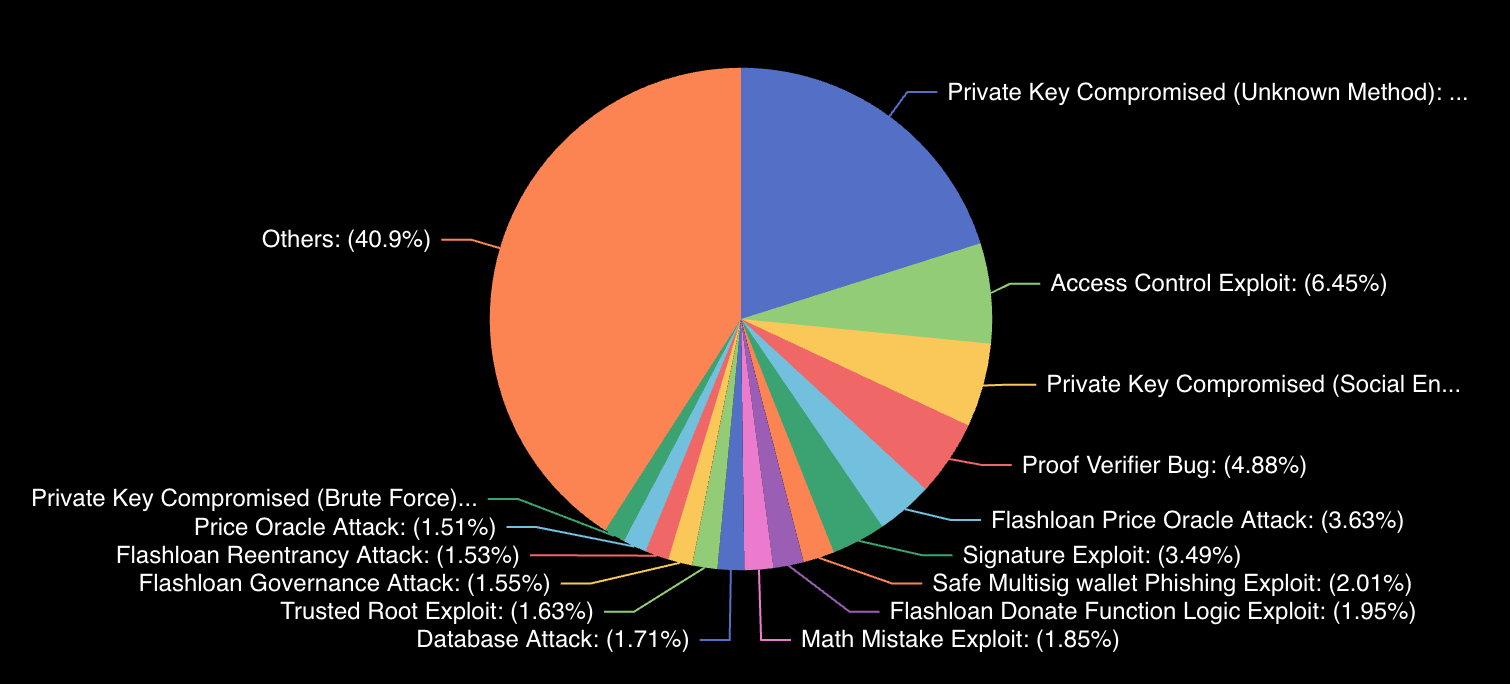 Fig. 2: Division of methods that led to significant hackingModern threats of today include:
Fig. 2: Division of methods that led to significant hackingModern threats of today include:- Access control failures: Inadequate privilege management was the primary cause of the DMM Bitcoin and WazirX exploit, as well as other significant losses in Q2 2024.
- Smart contract exploits: Attacks that took advantage of re-entrancy flaws and inadequate upgrade procedures cost over $67.4 million in Q2 2024 alone.
- Address poisoning: This method, which has become a significant threat, resulted in a single incident that cost $68.7 million in Q2 2024.
These evolving attack vectors underscore the critical need for proactive and verifiable security measures across the Crypto ecosystem.
Comparing Internet and Crypto AdoptionThe number of Bitcoin users has surpassed 35 million in a decade, more than double the internet’s early growth. Between 2018 and 2023, the number of people using PayPal, Visa, Mastercard, and American Express grew at an annual rate of 8%. However, the number of people who owned cryptocurrencies grew at a compound annual rate (CAGR) of 98%. This means new users and new capital, and a quickly increasing need for security.
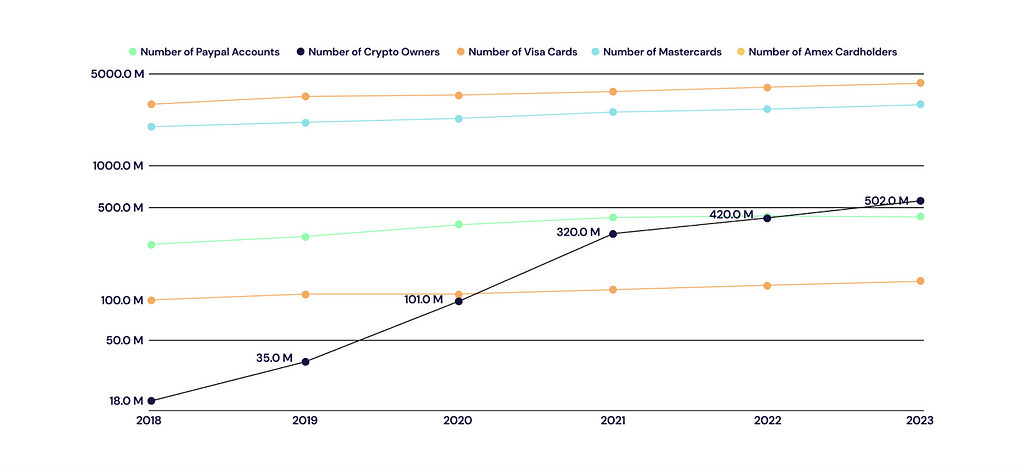 Fig. 3: Global crypto ownership growth
Fig. 3: Global crypto ownership growthThe parallels between the internet and crypto adoption are striking. While it took nearly 33 years for the internet to reach 5 billion users, that is 62.5% of the global population, cryptocurrency is on track to achieve a comparable level of adoption within the same period. Consider how the internet transformed the world, and imagine how crypto could similarly revolutionize our lives. Read here about how early tech and internet companies established their moats with security.
However, just as the internet’s growth brought with it phishing attacks, data breaches, and privacy concerns, the rapid expansion of cryptocurrency has also revealed new risks, which we are all too familiar with.
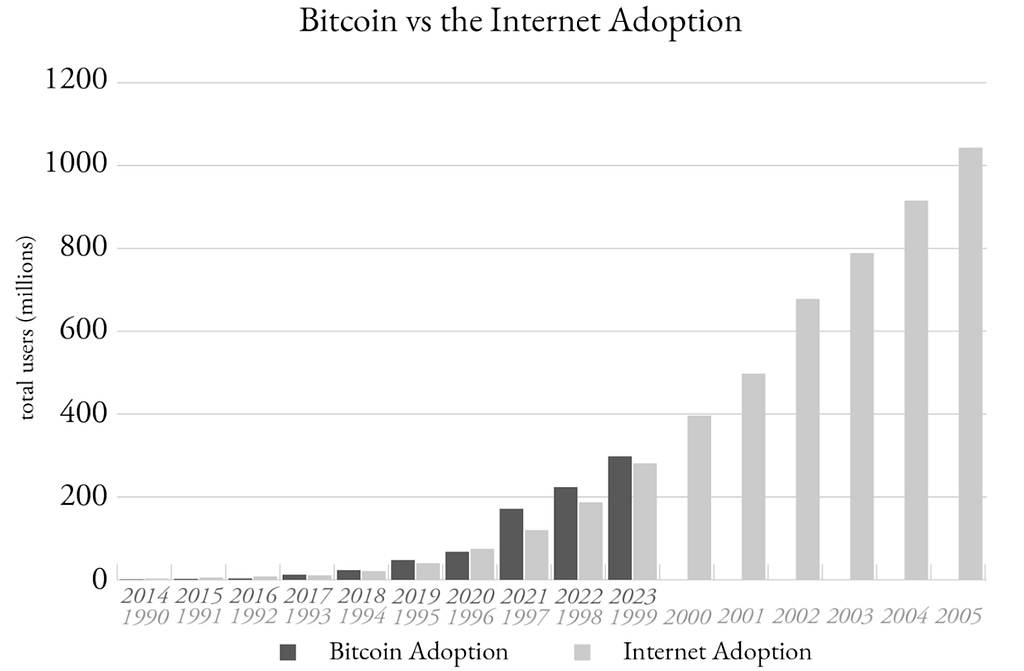 Fig. 5: DeFi adoption vs internet adoption curveWeb2 Security Adoption vs. Crypto
Fig. 5: DeFi adoption vs internet adoption curveWeb2 Security Adoption vs. CryptoWeb2 security frameworks were shaped by incidents such as the Silk Road marketplace and the MySpace worm. The Samy worm, which took advantage of cross-site scripting flaws, showed how easily malicious code could spread through social networks. This made people rethink how to keep websites safe in dynamic environments. Similarly, the Silk Road showed how important strong security frameworks are for stopping illegal activities on the internet, which led to better security features in Web 2.0 applications.
The DAO hack and the Ronin Network attack highlight the importance of proactive security in protecting decentralized ecosystems and their billions of users.
This is the trend that Crypto is following.
How security has changed in Web2 can help us understand how security will change in Crypto. Problems with the old internet led to the creation of the Payment Card Industry Data Security Standard (PCI DSS) and strong anti-malware protocols.
Now, Crypto is also defining its security standards, moving from isolated audits to code transparency, decentralized insurance, proactive security measures, and competitive audits.
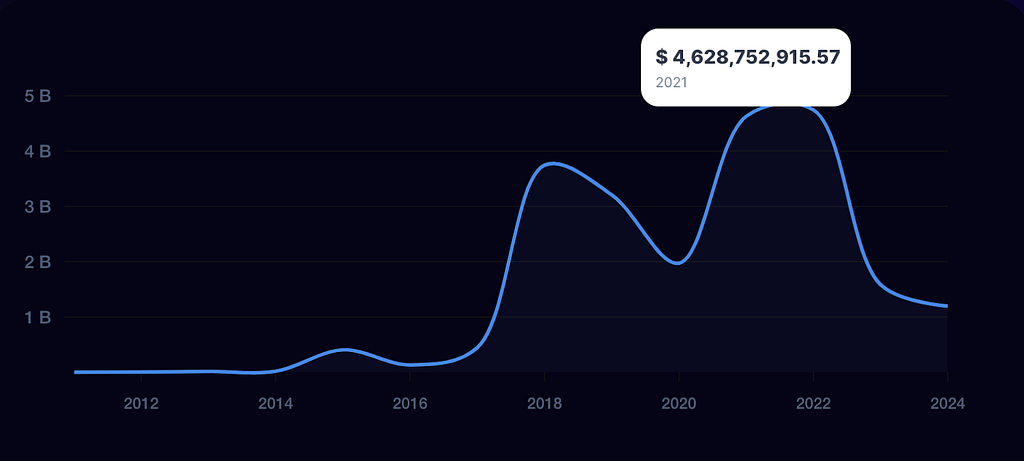 Fig. 4: Trends in the Amount Lost Over the Past Ten Years
Fig. 4: Trends in the Amount Lost Over the Past Ten YearsAs we can see from 2017 to 2021, during the crypto boom and the rise of numerous new projects, the crypto space faced significant challenges with security. The technology’s early-stage vulnerabilities and susceptibility to various attacks largely contributed to the hacking of many projects, resulting in staggering losses.
Since then, the industry has made notable progress. Security researchers, investigators, founders, investors, and projects have increasingly prioritized Crypto security, leading to a significant reduction in the amount stolen.
However, losses still amount to billions annually, highlighting the critical need for more comprehensive tools, robust reviews, and advanced monitoring frameworks to enhance fund recovery and overall security.
The adoption of these measures is essential to maintaining trust and accelerating mass adoption. The industry must come together around standards and frameworks for preventive security.
DeFi’s Transformative RiseThe integration of real-world value on-chain and the widespread adoption of blockchain technologies are two key trends propelling the revolutionary evolution of decentralized finance (DeFi). Tokenized markets, such as the $2 billion tokenized US Treasury market, are bridging traditional finance and blockchain, while on-chain solutions like Base and Ink are revolutionizing the storage, transfer, and use of value.
Base and Ink stand out from other L2 solutions due to their both being incubated by large, well-known CEXs. This is a sign that the future is on-chain.
Millions of new users are using blockchain apps for the first time, as 1 billion cryptocurrency users are projected by 2027. This wave of adoption presents a unique challenge: how to create a safe environment where users can explore technologies without losing their investments to exploits or poorly designed protocols.
Managing Risks in DeFiRecent attacks on cross-chain bridges and tokenization platforms have demonstrated the vulnerabilities inherent in transferring significant value on-chain.
DeFi’s complexity introduces several types of risk:
- Financial risks: platforms can become unstable due to market volatility and a lack of liquidity, which can lead to cascading failures.
- Smart contract risks: upgrades and contract flaws could result in disastrous fund losses.
- Off-chain security risks: wallet breaches, custody mistakes, and phishing attempts continue to be serious dangers.
Developers shouldn’t just rely on smart contract audits to protect the growing number of institutional and retail users. Instead, they should set up clear, safe systems with decentralized oracles, multi-signature wallets, and proactive monitoring tools.
Users should also implement proven security practices such as the use of hardware wallets and two-factor authentication. If either the user or the dApp fails in their attempt to stay secure, TVL goes to 0.
Recent Innovations in Crypto SecurityThe growing complexity of decentralized systems has prompted the creation of numerous new security solutions. Some of the key innovations in this space include:
Next-block Mitigation & Front-running Protection:The goal of these mechanisms is to stop attackers from taking advantage of predictable transaction behaviors. By concealing transaction details or building blocks that prevent malicious transactions from mining first, it offers vital protection against front-running and related exploits.
Fuzzing & Client-Side Monitoring:Fuzz testing has become a crucial tool for smart contract security, involving the use of random or unexpected inputs to uncover hidden vulnerabilities. However, it is important to note that fuzz testing is compute-intensive, requiring significant processing power to explore a wide range of potential edge cases effectively.
Additionally, client-side monitoring has proven highly effective in identifying potential issues in contract interactions with clients, allowing developers to address problems proactively before they escalate.
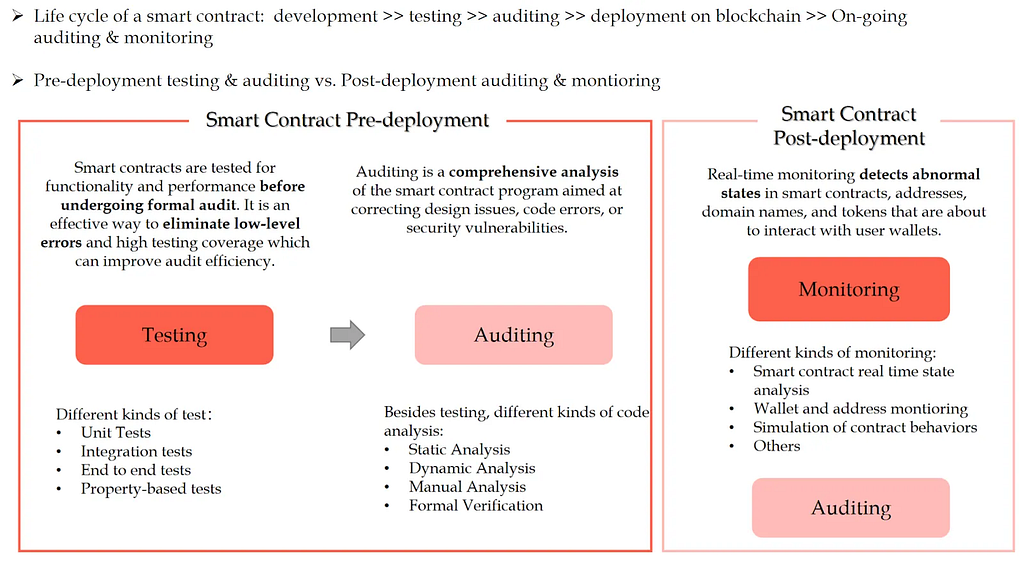 Fig. 6: Smart contract security life cycleHow Formal Verification Prevents Bugs
Fig. 6: Smart contract security life cycleHow Formal Verification Prevents BugsFormal verification is crucial to Crypto security, as shown by the recent compiler-level bug affecting Aave on ZKSync Era. Formal verification tools helped find the problem’s root cause: it was caused by a small optimization flaw in the LLVM compiler that created an incorrect bitmask dimension. This led to incorrect behavior in bit manipulation operations.
A “magic value,” which is a constant value, was hardcoded in the compiler’s optimization routine and caused the bug. This value, which is a 64-bit constant mask meant to clear certain bits, was used incorrectly in the 256-bit ZK-EVM environment. Because the higher-order bits were set to zero in the wrong way, lower-bit flags were cleared during bitwise operations without meaning to.
This example demonstrates how formal verification enables deep, low-level analysis, which traditional testing methods frequently overlook.
Bug Bounty and Audit CompetitionsIn recent years, the industry has grown significantly, which is indicative of how crucial security is becoming in the blockchain space. More than $100 million has been distributed to white-hat hackers through bug bounty and audit platforms thus far.
Platforms like Code4rena, Sherlock, and Cantina are gaining traction by offering pre-deployment security audits, where security researchers review code before it is made public. Together, these platforms have helped uncover over 1600 high-level bugs, over 30,000 unique findings, and secured billions of dollars.
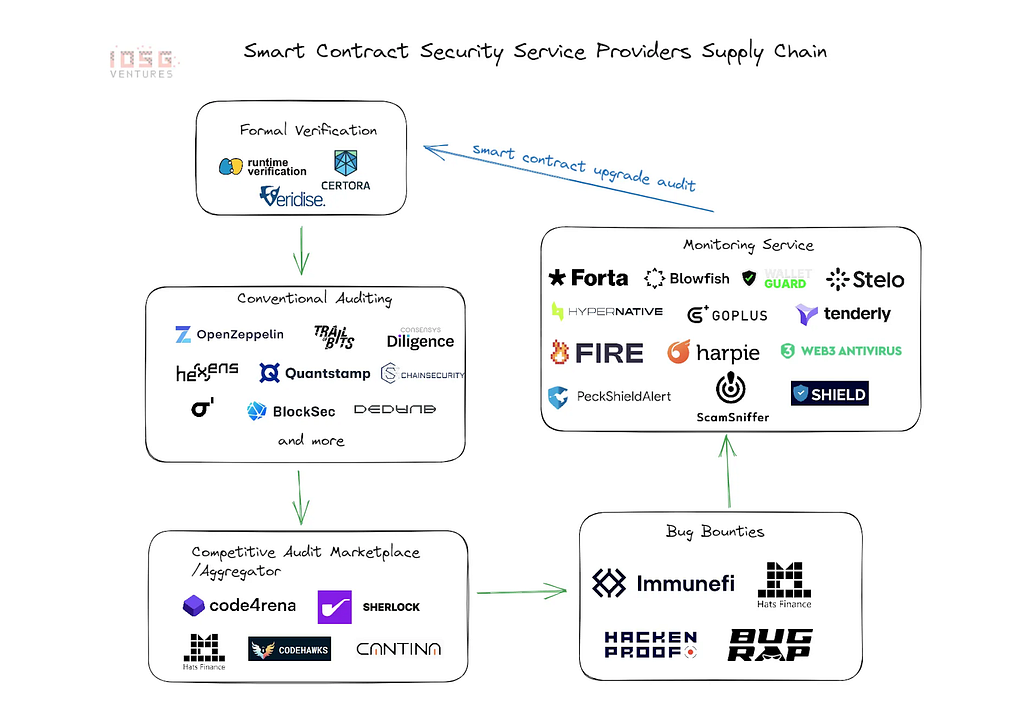 Fig. 7: Growth in Smart Contract Security Service Providers
Fig. 7: Growth in Smart Contract Security Service ProvidersNotably, platforms like Code4rena (recently acquired by zellic) are growing rapidly, having conducted over 418 audits to date, with projects like Opensea, Uniswap, and zkSync choosing them over traditional security firms due to the larger number of auditors they attract for reviewing the codebase.
Traditional post-deployment security solutions include bug bounty programs, which offer monetary rewards to ethical hackers who find vulnerabilities. Crypto leaders Immunefi and Hats Finance are setting the standard by providing bug bounty programs and fusing them with competitive audits for a more comprehensive security strategy.
Types of Hacks and Vulnerabilities in Crypto (2024)As Crypto matures, attacker strategies become more complex and focused. As an industry, we can reduce risks and make ourselves more resilient by learning about the most common types of vulnerabilities.
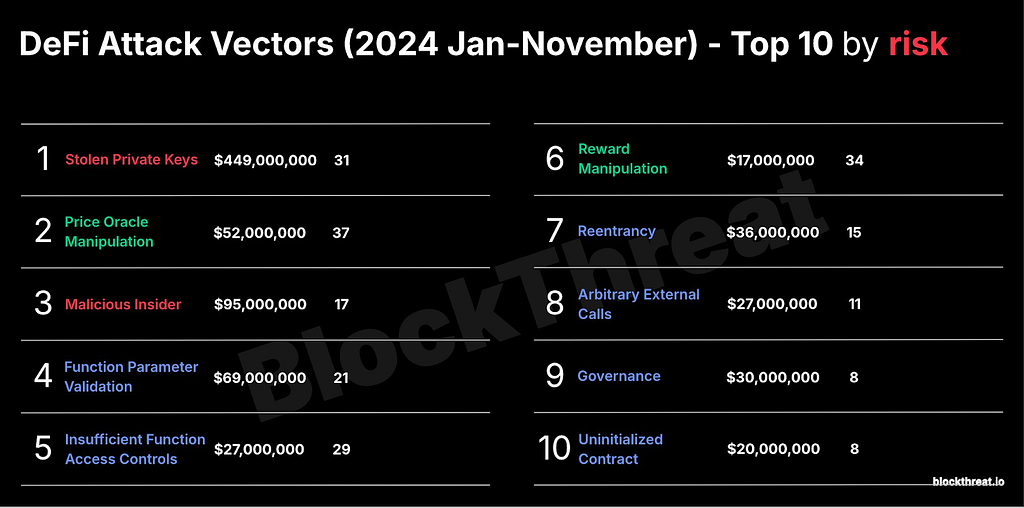 Fig. 8: Top Ten DeFi Attack Vectors in 2024.1. Re-Entrancy Attacks
Fig. 8: Top Ten DeFi Attack Vectors in 2024.1. Re-Entrancy Attacks- Uses recursive calls to get money out of the account before the state changes.
- On January 25, 2024, a reentrancy attack was used to steal $180,000 from Nebula Revelation.
- Due to unconfirmed custom code in dApps, it is uncommon but is making a comeback in niche DeFi platforms.
- Manipulates transactions by inflating asset values and taking advantage of price feed dependencies.
- Sonne Finance (2024) lost $20 million as a result of attackers inflating token prices in order to drain liquidity pools.
- Take out short-term loans with a lot of debt to take advantage of loopholes in the protocol.
- In 2024, a flash loan attack cost Gamma Strategies $6.4 million. This attack happened to a lot of big projects last year, including Euler Finance, Beanstalk, and Kyberswap.
- There have been fewer of these kinds of attacks since tech like loan caps was introduced.
- Using phishing, malware, or social engineering to get into high-value wallets and steal their information.
- In 2024, DMM Exchange lost $305 million, and in 2022, Ronin Network lost $625 million because of a private key breach.
- Continues to be the most serious threat, necessitating stringent operational security practices.
- Attackers can do things that are not supposed to be done when function-level permissions are weak.
- Duelbits lost $6.7M because wallets did not have enough privilege restrictions.
- Attackers are developing increasingly sophisticated techniques to bypass multi-factor authentication (MFA), exploiting weaknesses in implementation, social engineering, and authentication protocols.
- A scam where attackers send tiny transactions to a user’s wallet using addresses that closely resemble legitimate ones.
- The objective is to create confusion in the transaction history, leading users to mistakenly select the malicious address when copying.
- Caused a $69 million loss overall in the first half of 2024.
- Gaining traction as attackers take advantage of trust and user error.
A lot of projects still ask users to “just trust us” in an industry that was built on the idea that people should not need to trust each other. This paradox represents one of blockchain’s most pressing challenges. Think about these common situations:
- Teams are deploying unverified smart contracts.
- Protocols relying on centralized price oracles
- Projects with emergency admin keys
- Upgradeable contracts without timelock mechanisms
Each instance introduces trust assumptions that contradict blockchain’s foundational promise: verifiable trust through code. When is crypto going to make good on this promise?
Moving Towards Verifiable, Embedded SecurityIn today’s world, users can only check social media sites like Twitter, Telegram, Discord, or Reddit to find out if the protocol they are using has been hacked. This lack of transparency makes users vulnerable and unaware of potential threats to their funds and data. This is where verifiable security measures play a crucial role in ensuring that users can independently verify the security and integrity of the protocols they interact with.
Traditional trust assumptions frequently rely on a few centralized actors or unverified entities, which contrasts sharply with the ethos of underlying blockchain technology. Its systems may not be open or accountable, putting the industry at risk.
Putting in place verifiable security measures like cryptographic proofs and transparent assertion layers to lower these risks. These let users and developers check security claims on their own without having to rely on central authorities. This is how it appears in real life:
1. Cryptographic Proofs- Transaction integrity is validated by zero-knowledge proofs.
- State changes are confirmed by Merkle proofs.
- Formal verification of critical protocol components.
- Time-delayed upgrades
- Multi-signature requirements
- On-chain governance
- Public audit trails
- Cryptographic attestations
- Fraud proofs
Additionally, the level at which security guarantees are made is extremely important; for instance, sequencer-level security built right into the base layer is nearly impossible to bypass, making it very effective against hackers.
The more embedded security is, the better.
The “Don’t Trust, Verify” FrameworkBlind trust is greatly reduced when verifiable security is incorporated directly into protocols, creating a culture of do not trust but verify. This strategy strengthens the foundation of transparency and trustworthiness while also improving the overall security framework. Thus, it attracts retail and institutional players who demand higher digital asset security standards.
Modern protocols should enable users to verify:
- Current system state is accurate.
- All changes follow protocol rules.
- Admin actions are defined and transparent.
For developers:
- Document all trust assumptions explicitly
- Implement verification mechanisms at the protocol level
- Provide tools for users to validate security claims
- Build time delays into sensitive operations
For users:
- Question protocols lacking verification mechanisms
- Use available tools to validate security claims
- Understand the trust assumptions they’re accepting
- Prefer systems with built-in verification
Enabling users to verify more rather than asking them to trust less is the way of the future for blockchain security. Projects succeeding in this space will:
Make verification accessible to average users.
- Make it simple.
- Build security proofs into protocol foundations.
- Create transparent, auditable systems.
- Enable real-time validation of security claims.
What we cannot forget is that Crypto security is a never-ending game of cat and mouse between attackers and defenders. Attackers are always coming up with new ways to get around increasingly sophisticated defenses.
The adaptation cycle looks like this:
Attack → Defense → Innovation → New Attack VectorThis cycle serves as an example of an important reality: security is a process of constant adaptation rather than a final destination.
Every time defenses are broken, a new wave of sophisticated attacks comes out. Let us look at some common patterns and trends that have been seen and have had a big impact on the tools, protocols, and frameworks that make the industry strong:
1. Flash Loan Attacks (2020)- Initial Vector: Price manipulation via instant loans
- Defense: Price oracle improvements
- Evolution: Attackers developed multi-step arbitrage attacks
- Initial Vector: Front-running transactions
- Defense: MEV-resistant protocols
- Evolution: Sophisticated sandwich attacks
- Initial Vector: Validator compromises
- Defense: Multi-layer validation
- Evolution: Social engineering of validator operators
The security challenges of Crypto are very different from those of Web2. The absence of a central authority in Web3 decentralized systems makes it challenging to retrieve lost money. Web2 platforms, on the other hand, feature a central hub that makes dispute resolution simpler.
Crypto presents special challenges, such as the possibility of decentralized exchange (DEX) vulnerabilities and the risk of 51% attacks on consensus algorithms. As a result, it requires innovative solutions that prioritize transparency and community-driven oversight.
The differences are our strengths and weaknesses at the same time. More focus than ever is needed to solve the paintpoints and make good on the upsides of crypto.
Redefining Proactive Security with Credible LayerProactive security in Crypto demands a shift beyond traditional methods and tools. While AI and machine learning have their place, the real power lies in fundamentally rethinking the integration of security into blockchain systems. It needs to be embedded and verifyable.
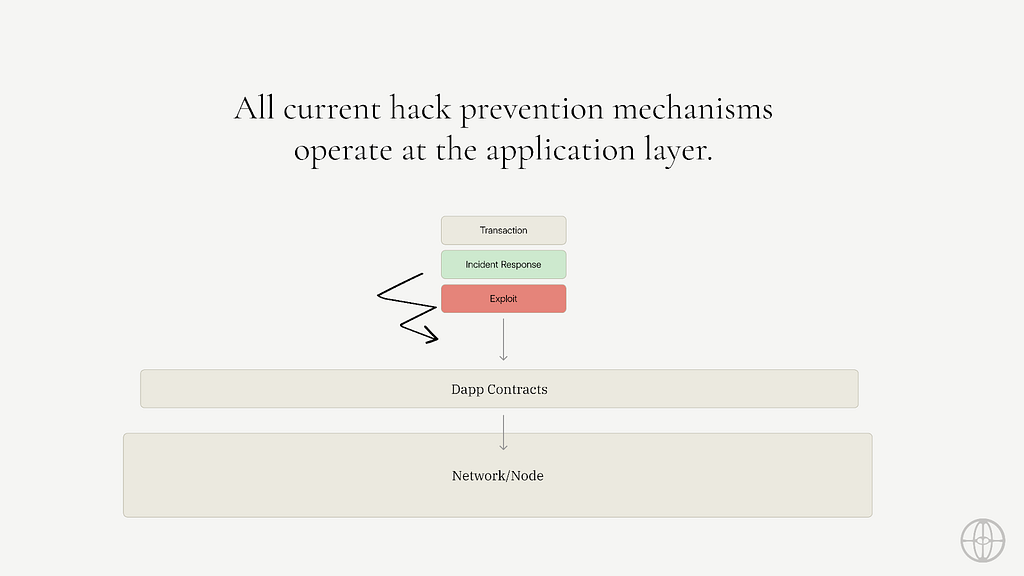
This is where the Credible Layer emerges as a groundbreaking solution, preventing hacks at the base layer.
The Credible Layer operates by enforcing provable assertions that allow dApps to define what constitutes a hack for their protocol. The block-building process validates these assertions, ensuring the detection and removal of malicious transactions before execution. Read more about how it works here.
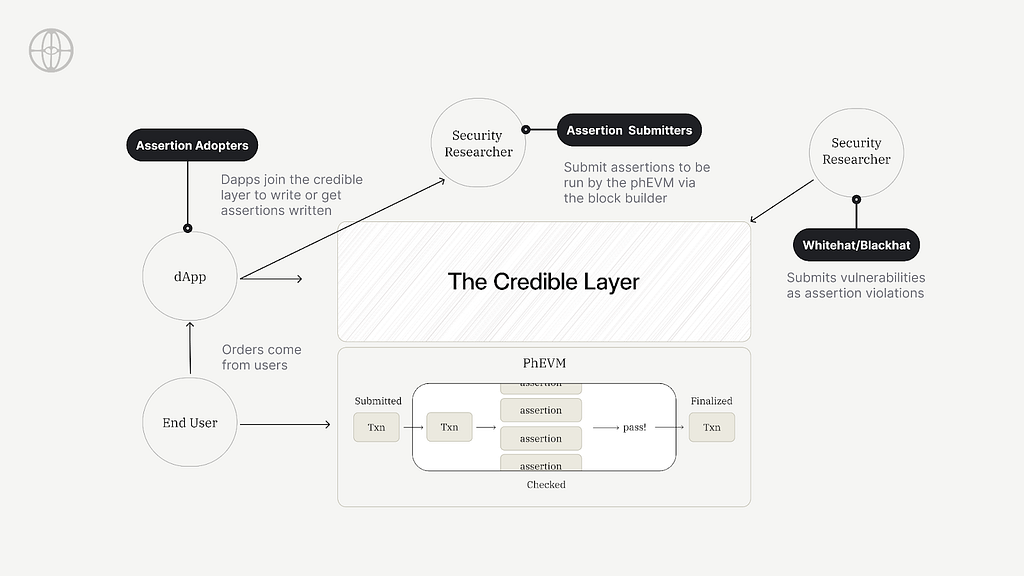
Unlike conventional security measures that rely on reacting to threats, the Credible Layer embeds protection directly into the infrastructure, enabling:
- Hack Protection at the sequencer level: Assertions added to the block validation process by block builders are the main defense against exploits. This stops exploits before they can ever affect the network.
- Transparency and Trust: Every assertion is publicly verifiable, enabling protocols and users to validate security measures independently without relying on centralized authorities.
- Sovereign and Powerful: dApps define their rules (“assertions”) in the form of EVM bytecode. These assertions define states that = hacks for the protocol and therefore should never be the result of a transaction. Only the dApp can enable assertions for their contracts.
This provable and embedded security model not only addresses immediate vulnerabilities but also builds a foundation of trust and reliability for dApps, protocols, and users alike.
By creating safer blockspace, the Credible Layer transforms security from a reactive afterthought into a proactive guarantee, enabling the blockchain ecosystem to scale with confidence.
Looking toward the next evolution of Crypto, the Credible Layer represents a transformative leap in securing decentralized systems, ensuring that innovation, adoption, and user trust are interdependent. This shift is not just necessary — it’s the cornerstone of blockchain’s future.
This article was created in collaboration with Phylax Systems. Special thanks to their team for their valuable insights and contributions to advancing Web3 security.Better security = more capital = more funds for dApps = more users = mass adoption.For users, enhanced security isn’t just about protecting assets—it's about trust. Cryptographic proofs transform the user experience from blind faith to verifiable confidence, making it as secure as traditional banking.
Thank you for reading ✌
